AI in Cybersecurity: Protecting Digital Assets
AI in Cybersecurity: Protecting Digital Assets with Strategic Innovation
Key Takeaways
Unlock the power of AI to revolutionize your cybersecurity approach and protect your digital assets with agility and precision. AI helps organizations protect their digital assets through advanced threat detection, prevention, and incident response capabilities. These insights focus on practical, scalable actions startups and SMBs can take now to build smarter, faster, and more adaptive defenses for 2025 and beyond.
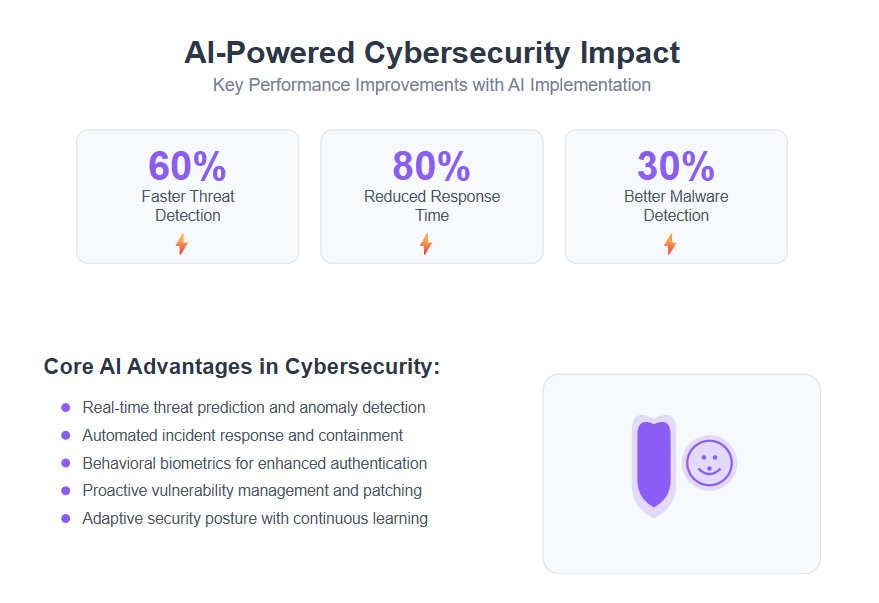
- Leverage AI-powered detection and automation to reduce threat identification times by up to 60% and cut incident response by as much as 80%, turning reactive security into proactive defense.
- Automate repetitive cybersecurity tasks with AI to reduce human error, improve efficiency, and enhance anomaly detection in security processes.
- Adopt behavioral biometrics and continuous AI-driven IAM to enhance authentication, reduce insider threats, and deliver seamless yet secure user experiences without friction.
- Prioritize AI tools that combine machine learning, predictive analytics, and automation to spot evolving threats—like zero-day exploits and AI-enhanced phishing—before they cause damage and enhance security by providing adaptive, proactive defenses.
- Balance automation with human oversight by implementing a human-in-the-loop approach that ensures critical decisions combine AI speed with expert intuition, minimizing false positives.
- Use AI for proactive risk and vulnerability management by focusing on high-risk gaps with intelligent prioritization and automated patching, improving security while optimizing limited resources.
- Integrate generative AI and blockchain technologies to achieve real-time transparency, fraud detection, and cryptographic verification that strengthen trust and compliance.
- Build an adaptive security posture that continuously learns from live threat intelligence and deploys dynamic defenses, including cyber deception and AI-driven threat hunting, to outpace attackers.
- Implement continuous training and measurement on AI workflows to empower your team, reduce alert fatigue, and iterate rapidly on security strategies using real-time metrics like MTTD and MTTR.
Ready to transform your cybersecurity into a proactive, AI-driven fortress? Dive into the full article to master the steps and tools that position your digital assets for resilient growth amidst evolving cyber threats.
Introduction
Imagine facing hundreds of cyberattacks every day—with alarms blaring, but your team buried under a mountain of false alerts. Sound familiar? For startups and SMBs, juggling fast growth with limited cybersecurity resources can feel like trying to catch smoke with your bare hands.
But what if your defense system could learn, adapt, and act faster than any human ever could? Artificial intelligence is now at the center of this transformation, serving as both a powerful tool for defenders and a method increasingly used by attackers to launch sophisticated threats.
The rise of AI-powered cybersecurity tools is transforming digital defense from reactive firefighting into strategic innovation. These smart systems don’t just chase yesterday’s threats—they predict, detect, and neutralize attacks in real time, all while freeing your team to focus on what matters most: building your business and protecting sensitive information such as personal data and confidential business records.
Here’s what you’ll discover:
- How AI leverages machine learning, automation, and predictive analytics to spot evolving threats before they cause damage
- Ways to accelerate incident response and reduce alert fatigue with intelligent automation
- Methods for smarter identity management that balance security and user experience
- Strategies to protect against sophisticated malware, phishing, and insider threats
- Insights into adaptive security postures, the applications and risks of AI technology in cybersecurity, and cutting-edge AI-blockchain integrations
What’s clear is this: ignoring AI in cybersecurity isn’t an option anymore. It’s about equipping your digital fortress with a guard that never sleeps—a defense that grows sharper as risks evolve.
Next, we unpack how AI is rewriting the cybersecurity playbook—turning overwhelming data into actionable intelligence, and turning your security challenges into opportunities for growth and resilience.
The AI Transformation of Cybersecurity: Foundations and Frameworks
In 2025, AI is fundamentally reshaping cybersecurity, turning traditional defenses on their head and setting new standards for protecting digital assets. A wide range of AI technologies, including machine learning, natural language processing, and predictive analytics, are now being deployed to enhance threat detection, automate responses, and improve overall security outcomes.
AI-driven tools tackle the key limitations of legacy approaches—slow response, overwhelming data, and static rule sets—by delivering speed, scale, and adaptability that humans alone can’t match.
Think of AI as a vigilant digital watchdog, analyzing vast, complex networks in real time to spot threats before they escalate, with AI's ability to detect anomalies and patterns that might otherwise go unnoticed.
AI-driven security systems are now foundational to modern cyber defense, providing proactive threat prevention and advanced protection against evolving cyber threats.
Core AI Capabilities Powering Cyber Defense
These foundational technologies define the AI advantage in cybersecurity by enabling systems to analyze vast amounts of security data:
- Machine learning (ML): Machine learning algorithms continuously learn from vast datasets and analyze vast amounts of data to recognize evolving threats without explicit programming.
- Predictive analytics: Uses historical attack data to forecast and prepare for potential breaches. Data mining is used to uncover hidden patterns in large datasets, informing proactive security measures.
- Automation: Executes immediate defensive actions like isolating compromised endpoints, slashing response times from hours to seconds.
Together, these capabilities enable organizations to shift from reactive security to proactive, strategic innovation—anticipating attacks rather than chasing them.
Picture a startup dealing with thousands of login attempts daily. Traditional logs drown staff in alerts, but AI tools surface only the truly dangerous anomalies, allowing teams to focus on real threats without burnout.
Why This Transformation Matters Now
- Cyber threats grow more sophisticated and frequent every year, costing businesses millions in damages.
- AI’s blend of real-time insights and automated defense means breaches can be detected and contained faster than ever, significantly strengthening cybersecurity defenses against sophisticated threats.
- SMBs and startups—often short on cybersecurity talent—gain enterprise-level protection through affordable, scalable AI systems.
For example, AI-powered detection has improved malware identification rates by over 30% compared to signature-based methods, cutting false alarms while boosting accuracy.
Curious how exactly AI sees threats others miss? Check out our deep dive: Why AI-Powered Threat Detection Is Revolutionizing Digital Security.
AI is no longer a futuristic option—it’s the foundation for resilient, next-gen cyber defense that adapts as fast as attackers evolve.
To function effectively, AI requires robust data and strong ethical frameworks to ensure both efficiency and responsible operation.
When you embed AI into your security strategy, you gain a partner that watches every corner of your digital footprint—so you don’t have to, while also improving your organization's security posture.
Invest in AI to move faster, scale smarter, and protect stronger in today’s turbulent cybersecurity landscape.
Advanced Threat Detection and Predictive Analytics: The First Line of Defense
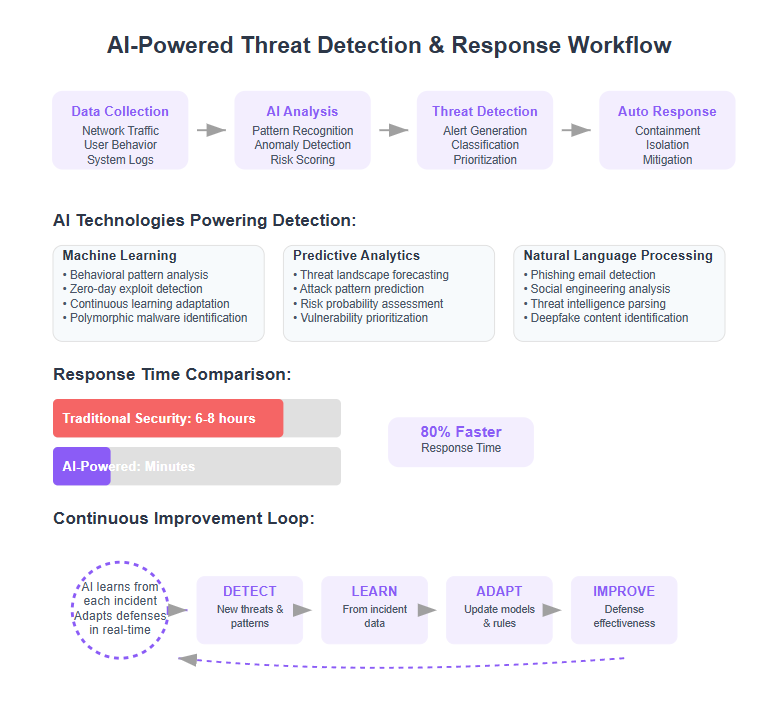
AI sifts through massive streams of network and user data in real time, using advanced analytics to identify patterns in network activity that may indicate threats, spotting threats far faster than human analysts could.
It watches for anomalies, unusual behaviors, and new attack patterns, and can spot emerging threats before they escalate—capabilities that would slip past traditional signature-based tools. This allows organizations to respond proactively to potential threats.
How Machine Learning Evolves Detection
By evolving with attackers and leveraging historical data to train detection models, machine learning pushes beyond outdated detection methods, giving you a dynamic shield that learns and improves continuously.
- Learns from evolving cyber threats and uses AI algorithms that analyze historical data to improve detection accuracy
- Detects zero-day exploits and polymorphic malware that change form
- Adapts to new phishing tactics and AI-driven social engineering scams
Predictive Analytics: Staying One Step Ahead
AI doesn’t just react; it anticipates cyberattacks by analyzing past incidents and using past data to forecast potential threats across industries.
This predictive intelligence highlights:
- Emerging ransomware strains
- Phishing campaigns exploiting global events
- Patterns in AI-powered social engineering attempts
- Analyzing patterns in attack data to predict future threats
Imagine your security system flagging a threat before it lands—cutting off infection before damage begins.
Balancing Alerts and Accuracy
The challenge? Avoiding alert fatigue by minimizing false positives without missing real threats.
The trick is:
- Combining AI detection with behavioral context
- Integrating insights seamlessly into existing Security Operations Centers (SOCs)
- Customizing alert thresholds based on your business environment
This balance ensures your team focuses on what matters most, gaining time and clarity.
Real-World Impact You Can Feel
Companies using AI-driven detection report:
- Up to 60% faster threat identification and response to security incidents
- Significant drops in successful phishing and malware breaches
Picture a dashboard lighting up only for genuinely dangerous events—cutting through noise and empowering swift action.
AI-powered threat detection creates a proactive fortress for your digital assets, turning overwhelming data into actionable defense. AI is also highly effective at blocking malicious traffic before it causes harm, providing automated protection against evolving threats.
Put simply: embracing AI means turning your security system into a watchful, learning partner that doesn’t sleep.
“AI is your digital security’s early warning system—catching threats before they knock.”
“Think of AI like a radar scanning for storm clouds you haven’t even spotted yet.”
“Cut alert noise, boost accuracy—AI helps your team work smarter, not harder.”
Automated Incident Response: Accelerating and Amplifying Cyber Defense
AI-driven automation is transforming incident response by enabling real-time actions the moment a threat appears. Automated processes streamline incident response by quickly isolating infected systems, blocking attacks, and containing damage without waiting for human analysts.
By automating these responses, AI frees up human analysts to focus on critical tasks that require expert judgment and strategic decision-making.
Speeding Up Response Time
Immediate containment is critical. AI’s ability to act within seconds dramatically reduces the window for attackers to cause harm.
Key benefits include:
- Instant system isolation to stop spread
- Automated threat blocking before manual review
- Streamlined containment protocols triggered without delay
When a ransomware attack hits, for example, AI can quarantine the targeted endpoint and sever its connection, preventing lateral movement that often leads to severe breaches.
Automating Complex Workflows
AI doesn’t just handle simple tasks. It can automate repetitive cybersecurity tasks and manage entire incident response workflows by:
Collecting forensic data
Collecting and analyzing security logs
Alerting SOC teams
Orchestrating remediation steps
This helps security operations centers (SOCs) handle higher volumes and complexity without burnout.
Research from 2024 shows well-implemented automation cuts response times by up to 80% and reduces breach costs by millions.
Balancing Human Oversight
Not every incident needs fully autonomous handling. A human-in-the-loop approach combines AI speed with expert intuition. Automation in incident response helps reduce human error by minimizing manual tasks that can lead to mistakes.
Considerations include:
- When to escalate alerts for human review
- Which threats AI can neutralize autonomously
- Avoiding “alert fatigue” through accurate automation
- When human intervention is necessary for complex or ambiguous incidents
This balance ensures speed without sacrificing decision quality, crucial for complex or novel attacks.
Real-World Visualization
Picture your security system as a self-driving emergency crew: AI spots the fire, calls for backup, and begins dousing flames before you even notice smoke.
It’s faster, smarter, and keeps damage minimal.
AI-enabled automated incident response is a game-changing layer of defense. It delivers instant threat blocking, drastically reduces response times, and frees up your team to focus on sophisticated threats.
Ready to supercharge your cyber defense? Automation is your new best friend in the security operation center’s toolkit.
Enhancing Identity and Access Management (IAM) with AI
AI is transforming Identity and Access Management (IAM) by making authentication smarter and security tighter without sacrificing user experience. Multi-factor authentication, which integrates biometric data and AI-powered solutions, is now essential in modern IAM to add extra security layers beyond traditional passwords. Behavioral biometrics and continuous verification now let systems confirm identities based on patterns—not just passwords.
AI-driven IAM also helps secure financial transactions by verifying user identities in real time, enhancing protection against unauthorized access and fraud.
Smarter Authentication with Behavioral Biometrics
Instead of relying solely on passwords, AI systems analyze how users interact with apps and devices:
- Typing speed and rhythm
- Mouse movement patterns
- Touchscreen pressure and gestures
This ongoing assessment creates a unique “behavioral fingerprint.” If something feels off—like a login at an unusual time or from an unfamiliar device—AI flags it instantly.
AI also detects compromised credentials by spotting unusual access attempts dynamically, helping prevent breaches caused by stolen passwords or leaked databases.
Use Cases Driving Security and Usability
AI-driven IAM solutions combine several techniques for thorough protection:
- Device fingerprinting to recognize trusted hardware
- User behavior analytics that spot anomalies during sessions
- Risk-based authentication which adjusts verification requirements based on real-time risk scoring
This approach allows for seamless access when everything checks out, but steps up defenses when something suspicious emerges.
Cutting Insider Threats with Continuous Monitoring
Insider threats often fly under the radar. AI monitors access patterns and flags:
- Sudden increases in data downloads
- Unusual file access sequences
- Attempts to bypass security protocols
By spotting these signs early, organizations reduce the risk of opportunistic or malicious insider damage.
Balancing Security and User Experience
One standout effect of AI-enhanced IAM is improved usability paired with tighter controls. Users avoid frustrating multiple password resets or complex 2FA steps unless a genuine risk is detected. This dynamic flow keeps friction low without sacrificing protection.
Think of it as a smart gatekeeper who recognizes trusted visitors instantly but raises the alarm for odd behavior. For startups juggling growth and security, AI-driven IAM helps stay agile while defending against increasingly sophisticated cyber threats.
"AI makes identity verification both invisible and intelligent—a game changer for access security."
"Continuous behavioral analysis means no more ‘one-size-fits-all’ passwords slowing you down."
Crafting IAM solutions that adapt in real time is no longer optional—it’s essential for protecting digital assets efficiently and confidently.
AI-Powered Protection Against Sophisticated Malware, Phishing, and Insider Threats
AI is rewriting the rulebook for malware and phishing detection, leaving behind clunky signature-based systems that can’t keep up with evolving threats, especially sophisticated attacks that use advanced techniques to bypass traditional defenses.
Instead, AI uses machine learning and natural language processing (NLP) to spot phishing emails and spear phishing attempts with pinpoint accuracy. AI-based systems provide scalable, real-time protection by detecting, preventing, and responding to threats as they emerge.
Smarter Detection with AI
Here’s how AI is stepping up:
- Beyond Signatures: It recognizes new malware variants by analyzing behavior patterns instead of relying on known malware signatures.
- Phishing Identification: NLP helps decipher email content, spotting subtle cues in phishing attacks that fool traditional filters.
- Deepfake Social Engineering: AI flags synthetic voices and video-based scams that try to trick employees into divulging sensitive data.
Think about how a fake CEO voice on a call could cost millions—the AI systems catch these deepfake scams before damage is done.
Insider Threats Under the Microscope
AI doesn’t just watch for external bad actors; it monitors user behavior across networks to detect insider threats, whether accidental or malicious.
It looks for unusual access patterns like:
- Sudden bulk downloads
- Off-hours logins
- Odd file-sharing activity
This real-time scrutiny alerts security teams before insider mishaps turn into breaches.
Proof in the Numbers
Several organizations cut data theft by upwards of 30% using AI-driven monitoring combined with behavioral analytics.
For example, a mid-sized fintech firm reduced fraud-related losses by 40% within six months after deploying AI tools capable of flagging subtle phishing and insider risks.
Key Takeaways You Can Use Today
- Upgrade from signature-based antivirus to AI-powered detection tools to catch novel malware and phishing attacks dynamically.
- Implement behavioral analytics to spot insider threat red flags early and reduce risk.
- Use AI-driven NLP capabilities to flag phishing attempts that slip past conventional filters.
Picture this: your SOC team receives an alert about an odd login late at night, automatically isolating the affected systems—stopping a breach before it starts. That’s AI in action, working as your digital watchdog 24/7.
The power of AI in detecting sophisticated threats lies in continuous learning and rapid adaptation, turning your cybersecurity from reactive to proactive in 2025.
Adaptive Security Posture: Dynamic Defense in an Evolving Threat Landscape
An adaptive security posture means your defenses aren’t fixed—they evolve constantly, fueled by AI’s ability to learn from live threat intelligence and attack patterns. AI processes vast amounts of threat intelligence data, enabling it to identify patterns and anomalies more effectively. This real-time learning allows security protocols to update on the fly, especially crucial against zero-day exploits and new threats that require adaptive, real-time defenses, which often surprise traditional static systems.
Constant Updates and Blockchain Synergies
AI-driven systems continuously refine protection by:
- Applying real-time updates to firewalls, access controls, and detection rules
- Reacting instantly to new attack methods detected anywhere on the network
- Integrating with blockchain technologies for stronger digital asset authenticity and traceability
Imagine your system instantly flagging a suspicious transaction and verifying its origin within seconds, thanks to blockchain’s immutable ledger linked with AI’s smart analysis.
Challenging Static Defenses with Dynamic AI
Traditional security setups are like locked doors—effective until someone picks the lock. AI-fueled defenses behave more like a smart home that recognizes unusual activity and adapts security measures immediately.
Key dynamics include:
- Continuous learning from evolving threats rather than static rulebooks
- AI-powered cyber deception, deploying adaptive decoys that confuse attackers and reveal their tactics
- Use of natural language processing (NLP) to sift through threat intelligence reports automatically, spotting emerging risks faster than humans can
The AI Arms Race: Attackers vs Defenders
We’re witnessing an accelerating arms race where attackers also use AI to craft more sophisticated methods. That means defenders must keep innovating, relying on AI’s speed and scale to defend at machine-level pace.
Some frontline realities include:
- Attackers employing AI-generated phishing and deepfake scams
- Defenders deploying automated adaptive protocols that shift based on attacker behavior
- Growing investments in AI-powered threat hunting and cyber deception to outsmart evolving threats
“Adaptive security isn’t just about responding faster—it’s about staying one step ahead by learning and evolving in real time.”
Picture this: A security system that senses an odd login, instantly deploys decoy data, and triggers a lockdown—all before a human even sees an alert.
Summary Takeaway
In 2025, a dynamic AI-driven security posture is non-negotiable for companies serious about digital asset protection. It’s about constant adaptation, real-time learning, and embracing new tools like blockchain and cyber deception to outpace threats before damage happens. Your defense isn’t a wall anymore—it’s a living, breathing shield that changes as fast as the threats you face.
Proactive Risk and Vulnerability Management with AI Insights
AI is transforming how businesses identify and manage cybersecurity risks before they escalate into breaches, helping organizations protect their assets by proactively identifying and managing risks.
By continuously scanning your environment, AI tools assess, prioritize, and predict vulnerabilities based on their potential impact—not just their presence on a checklist. This means you’re focusing resources where it counts. AI-driven risk management also enhances security by prioritizing critical vulnerabilities, enabling more adaptive and effective defenses.
Intelligent Prioritization and Patch Management
Instead of drowning in endless security alerts, AI-driven platforms help you:
- Prioritize vulnerabilities by risk score and exploit likelihood
- Automate patch scheduling to close critical gaps faster
- Allocate security resources efficiently to high-risk areas
For example, AI can flag a recently discovered software flaw widely exploited in the wild, ensuring your team patches it immediately—preventing costly exploits.
Early Detection and Business Alignment
AI's predictive abilities allow early identification of high-risk exposures behind the scenes, catching threats before attackers do.
At the same time, these systems:
- Align monitoring efforts with your company’s compliance needs and business priorities
- Trigger alerts tailored to what matters most for your operations and industry standards
Imagine AI understanding your unique environment so well, it knows which vulnerabilities could derail your next product launch or impact customer data privacy.
Fostering a Risk-Aware Culture with AI Intelligence
Risk management is not just tech—it's a mindset. AI insights provide your team with clear, actionable intelligence, creating a culture where risk awareness is built-in.
This kind of intelligence empowers your whole organization to:
- Take ownership of security roles confidently
- React dynamically as AI updates threat assessments in real time
Shareable Takeaways
"AI doesn’t just find vulnerabilities — it sharpens your focus on what truly matters."
"Streamlining patch management with AI can cut breach risks by addressing critical gaps within hours, not weeks."
"Early risk detection powered by AI transforms reactive security into proactive defense."
Picture this: your security team going from overwhelmed to focused, using AI-powered dashboards that highlight the top five vulnerabilities demanding immediate action.
This approach is especially valuable for SMBs and startups aiming to keep costs down while maximizing impact.
Whether you’re scaling rapidly or tightening governance, proactive vulnerability management with AI is about working smarter, not harder.
Want to dive deeper? Check out “Unlock the Power of AI for Proactive Digital Asset Protection” for real-world strategies and tools to build your strongest defense yet.
Harnessing AI in risk and vulnerability management puts you ahead of attackers by turning data into foresight—and foresight into action.
Integrating Generative AI and Blockchain for Next-Gen Cybersecurity
Generative AI is stepping up as a powerful tool for anomaly detection in complex digital asset markets. It spots unusual patterns that might signal fraud or manipulation faster than traditional monitoring methods.
Advanced encryption techniques, including quantum-resistant encryption algorithms and post-quantum cryptography, are becoming essential for securing digital assets against future quantum computer attacks.
When paired with blockchain’s immutable ledger, AI delivers transparent, real-time insights into digital transactions that are nearly impossible to tamper with.
Real-Time Transparency with AI and Blockchain
The combination offers:
- Instant fraud detection across financial platforms
- Continuous tracking and verification of supply chain events
- Secure, auditable records for public sector applications
This synergy not only enhances trust but also speeds up intervention by flagging suspicious activity as it unfolds.
Enhancing Trust Through Cryptographic Verification
AI's ability to verify transactions cryptographically ensures authenticity and guards against forgery or deepfake social engineering attacks.
- Blockchain secures data integrity by design
- AI analyzes transaction histories for behavioral patterns
- Together, they reduce risk and simplify compliance with industry regulations
Picture this: a supply chain manager watching a live AI dashboard, instantly alerted to a potentially compromised shipment traceable on a blockchain they trust implicitly.
Real-World Applications Driving Innovation
Across industries, AI-blockchain integrations are gaining traction:
Financial services use it to combat money laundering and unauthorized transfers
Government agencies rely on it for transparent record-keeping and fraud prevention
Manufacturing secures product authenticity and monitors logistics
Recent studies highlight a 40% reduction in fraud losses within six months after adopting these combined systems.
This powerful duo marks a new frontier in cybersecurity, where transparency meets predictive intelligence.
Think of generative AI and blockchain as the ultimate tag team unlocking next-level protections—transforming live data into actionable intelligence with an unbreakable chain of trust.
By mastering this combo, startups and SMBs can not only protect digital assets better but also build customer confidence in an increasingly digital world.
Embracing generative AI and blockchain today means positioning your security to adapt and evolve in real time—because cyber threats aren’t waiting, and neither should you.
Industry-Leading AI Cybersecurity Solutions: Tools Powering Innovation in 2025
The top AI cybersecurity platforms in 2025 are busy rewriting the rules on how digital assets stay safe. Names like Darktrace, IBM Watson, CrowdStrike Falcon, Microsoft Security Copilot, and PentestGPT are leading the charge, delivering capabilities that feel like having a 24/7 digital security team at your fingertips. Cybersecurity teams leverage these platforms for advanced threat detection, monitoring, and rapid response.
As these solutions evolve, the importance of skilled cybersecurity professionals in managing AI-driven tools becomes even more critical, ensuring that human expertise complements automated defenses for optimal protection.
Powerful Capabilities at Your Command
These solutions bring a suite of features designed to tackle today’s evolving threats:
- Endpoint protection that stops threats before they spread
- Threat hunting powered by machine learning to spot hidden dangers
- Penetration testing automated for faster vulnerability discovery
- Security operations center (SOC) optimization that streamlines analyst workflows
Imagine your startup’s system automatically detecting a phishing attempt and isolating it within seconds—that’s the kind of proactive defense these platforms enable.
Choosing the Right Fit for SMBs and Startups
Affordability and scalability matter, especially when resources are tight. Startups and SMBs should prioritize:
Automation capabilities to reduce manual monitoring time
Integration ease with existing tools and workflows
Transparent, usage-based pricing that scales as your company grows
A nimble AI-powered solution can shorten breach detection times by up to 60%, saving money and reputation.
Real Stories, Real Impact
Take a fintech startup that integrated Microsoft Security Copilot—it cut incident response time by 50%, allowing their team to focus more on product development. Or an SMB using Darktrace that thwarted a ransomware campaign before it caused damage, thanks to AI’s anomaly detection.
These wins aren’t just numbers—they’re the difference between scrambling after an attack and sleeping soundly knowing AI has your back.
AI-driven cybersecurity tools aren’t just fancy add-ons; they’re strategic partners that empower teams to act faster, smarter, and with confidence. For startups and SMBs ready to scale securely, picking the right platform is your first smart move toward a future where AI handles the grunt work and you focus on innovation.
Ethical and Practical Considerations in Deploying AI for Cybersecurity
AI is a powerful tool in cybersecurity, but deploying it without care can raise significant ethical and practical challenges. Establishing robust ethical frameworks is essential to guide the responsible development and deployment of AI systems in this field.
Balancing Innovation with Privacy and Ethics
The tension between advancing defenses and respecting user privacy is real. Using AI to monitor behavior risks overreach if not carefully managed.
Key considerations include:
- Avoiding invasive data collection that violates user trust
- Ensuring AI decisions don’t unfairly target or discriminate against certain groups
- Maintaining transparency in how AI models make security choices
Picture this: an AI system flags suspicious activity—great. But if it wrongly targets an employee based on biased data, that can harm careers and morale.
Addressing Bias, False Positives, and Transparency
AI systems often inherit biases from their training data, leading to false positives or unfair profiling.
To minimize risk:
Regularly audit AI models for bias
Tune systems to balance detection accuracy and false alarm rates
Provide clear explanations for AI-driven alerts so security teams can make informed decisions
This keeps AI from being a black box and ensures teams trust the system rather than dismiss alerts out of frustration.
Human Oversight and Accountability
Even with automation, human judgment remains crucial.
- Humans must verify critical AI-driven decisions
- Accountability should be clearly assigned to prevent responsibility gaps
- Establish “fail-safes” to catch AI errors before they cause damage
Think of AI as your co-pilot, not the autopilot—it guides you but doesn’t replace your judgment.
Legal and Regulatory Considerations
AI cybersecurity tools must comply with evolving regulations:
- Data protection laws like GDPR and CCPA dictate how data can be used
- Security standards require documenting AI decisions during audits
- Staying ahead legally means designing AI solutions with compliance baked in
Ignoring this can lead to costly fines or lost business trust.
Fostering a Culture of Responsible AI Use
Security teams should:
- Encourage ongoing training on ethical AI use
- Promote transparency in AI deployment decisions
- Share lessons about AI successes and failures openly
This builds a culture where AI enhances security without compromising values.
Ethics and practicality go hand in hand when deploying AI for cybersecurity. Prioritize transparency, bias mitigation, human oversight, and compliance to make AI a trusted shield for your digital assets. This approach turns innovation into a strategic advantage without sacrificing integrity or accountability.
Five Essential Steps to Building an AI-Driven Cyber Defense Strategy in 2025
Startups and SMBs can no longer afford to wait on traditional cybersecurity methods. AI relies on large datasets for effective threat detection, enabling advanced pattern recognition but also introducing challenges related to data quality and privacy.
AI-driven defense is not just the future—it’s today’s necessity for protecting digital assets efficiently and confidently. When building your strategy, consider all the benefits and risks of AI adoption to ensure a balanced and secure approach.
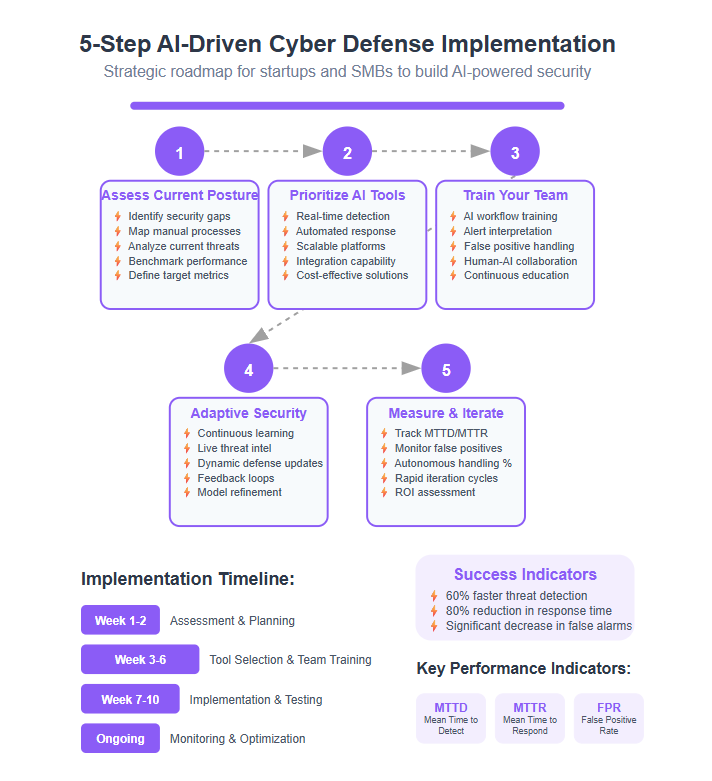
Step 1: Assess Your Current Cybersecurity Posture
Begin by mapping out your existing security setup and pinpointing gaps AI can fill.
Ask questions like:
- Where do manual processes slow you down?
- What threats slip past your current tools?
This gives you a clear target for AI integration and a benchmark to measure improvement against.
Step 2: Prioritize AI-Integrated Tools for Detection and Response
Focus on tools that deliver real-time threat detection and automated incident response.
Look for platforms offering:
- Machine learning-driven anomaly detection
- Automation in containment and remediation workflows
Remember, investing in AI that scales with your growth is critical—don’t get stuck with rigid solutions.
Step 3: Train Your Team on AI Workflows
AI doesn’t replace expertise—it amplifies it. Train your team to:
Understand AI alerts and data outputs
Manage false positives without alarm fatigue
Monitor AI-driven processes for unexpected behavior
Effective training turns AI into a powerful teammate, not a black box.
Step 4: Implement Continuous Learning and Adaptive Security
AI works best when it learns and adapts from live data.
Set up protocols for:
- Regularly updating AI models with new threat intelligence
- Tweaking response playbooks based on incident outcomes
- Encouraging feedback loops within the security team
This keeps your defense sharp against evolving cyber threats.
Step 5: Measure Outcomes and Iterate Rapidly
Track metrics like:
- Mean time to detect (MTTD) and respond (MTTR)
- Reduction in false positives
- Percentage of incidents handled autonomously
Use this data to refine your AI strategy continuously. Think of it as sprint cycles in your cyber defense: assess, act, improve, repeat.
Real-World Snapshot:
Imagine cutting your incident response time from hours to minutes, preventing a ransomware attack before it encrypts critical data—that's the power of AI automation paired with proactive strategy.
“Adopting AI in cybersecurity isn’t a one-and-done deal. It’s a dynamic journey where learning and action happen in real time.”
Taking these five steps helps you build a resilient, AI-powered cyber defense that evolves as fast as threats do—making AI your ride-or-die partner in digital security.
For detailed checklists and step-by-step guidance, check out Mastering AI-Driven Cyber Defense: 5 Essential Steps for 2025.
Conclusion
Embracing AI in cybersecurity isn’t just a smart upgrade—it’s your frontline partner in protecting digital assets with unmatched speed, precision, and adaptability.
By leveraging intelligent automation, real-time threat detection, and adaptive defenses, you transform security from a reactive burden into a proactive innovation engine that scales with your business.
Here’s how to put this into action today:
- Identify key security gaps where AI can amplify detection and response—start small but think big.
- Invest in AI-driven tools that offer seamless automation and continuous learning to stay ahead of evolving threats.
- Empower your team with AI training focused on managing alerts and interpreting insights effectively.
- Integrate adaptive security practices that evolve as your attack surface and threat landscape change.
- Measure outcomes rigorously and refine your approach—treat your cyberdefense like a sprint that iterates rapidly.
Take the leap now by auditing your current cybersecurity posture and exploring AI solutions tailored for SMBs and startups—your future-proof defense starts with curiosity and decisive action.
Remember: AI doesn’t replace your expertise—it supercharges it, freeing you to focus on innovation while your cyber defenses learn and adapt around the clock.
In the relentless game of digital security, staying still means falling behind. Move faster, defend smarter, and build with confidence—because AI is the ally that never sleeps.
FAQ — AI in Cybersecurity: Protecting Digital Assets
1) How does AI integration in cybersecurity actually work?
AI integration weaves together machine learning, predictive analytics, and workflow automation to elevate cyber defense from reactive to proactive. Machine learning for zero-day exploit detection analyzes behavior (not just signatures) to spot novel malware and lateral-movement patterns. Predictive analytics for cyber threat detection correlates historical incidents, threat intel, and live telemetry to forecast attack paths and flag high-risk anomalies earlier. Automation then executes policy-safe actions—quarantining endpoints, revoking tokens, or blocking IPs—so response begins in seconds, not hours. For startups, this translates into fewer manual checks and faster mean time to detect (MTTD) and respond (MTTR). Real-world rollouts consistently report up to 60% faster identification and 80% faster response, while reducing alert noise via context-aware scoring. The result is a unified defense fabric across endpoints, identities, email, data, and network. Paired with AI-driven vulnerability management and patching, teams prioritize the riskiest exposures first. In short, AI transforms sprawling logs into prioritized actions and turns your security stack into a continuously learning, high-signal early-warning system.
2) How much time can AI save in detection and incident response?
A well-implemented AI in automated incident response (2025) pipeline typically compresses MTTD/MTTR by wide margins: organizations see up to 60% faster threat identification and up to 80% faster containment compared with manual triage alone. Gains come from three levers: (1) continuous anomaly detection that surfaces truly suspicious events (not every spike), (2) playbook automation that instantly isolates compromised hosts, suspends risky sessions, or rotates credentials, and (3) enriched context (asset criticality, exposure, blast radius) so analysts decide faster. In ransomware scenarios, automated micro-segmentation and EDR isolation can halt spread within minutes. For phishing, NLP-based classifiers down-rank benign messages and fast-track high-risk ones to sandboxing. Importantly, automation doesn’t replace humans; it front-loads the investigation—collecting forensics, correlating alerts, and proposing next steps—so analysts spend time on judgment, not grunt work. For SMBs, these efficiencies free scarce talent, reduce overtime, and materially lower breach costs while improving sleep-through-the-night reliability.
3) What level of human oversight is required with automated AI?
Automation should accelerate action, not bypass accountability. The pragmatic model is human-in-the-loop: AI executes low-risk, reversible steps (e.g., quarantine an endpoint, block a domain) while routing irreversible or business-impacting actions for analyst approval. Calibrate this with risk-based guardrails: crown-jewel systems, VIP accounts, or production databases require extra verification; routine commodity malware can be auto-remediated. Mature programs also implement approval tiers, audit trails, and automatic rollbacks to ensure recoverability. Practically, analysts review AI-generated rationales (features, correlations, precedent cases) before confirming escalations. Over time, feedback retrains models, shrinking false positives and sharpening precision. The goal isn’t to trust a black box; it’s to make expert judgment faster and better informed. Expect automation to handle data gathering, evidence packaging, and first-response actions; humans arbitrate ambiguous signals, policy exceptions, and novel TTPs. This balance pairs machine-speed containment with expert stewardship, reducing fatigue while preserving control and compliance obligations.
4) How does AI minimize false positives and algorithmic bias?
Reducing noise starts with behavioral baselining: models learn normal per-user, per-device, and per-service patterns, so deviations carry context (new geos, unusual data volumes, atypical hours). Feedback loops then label outcomes (true/false positive), continuously improving precision. To curb bias, follow ethical AI deployment in cybersecurity: (1) diversify training data to avoid overfitting to a cohort, (2) use interpretable features and provide analyst-readable explanations (why the alert fired), (3) monitor drift and recalibrate thresholds when environments change (M&A, remote shifts, new SaaS). Blend multiple signals—identity risk, endpoint telemetry, data access, and email NLP—to avoid single-channel overreaction. Finally, instrument review workflows: when analysts dismiss an alert, that negative signal updates the model; when they confirm, the pattern receives higher weight. Programs combining model governance, transparent scoring, and analyst feedback routinely cut false positives by double digits, preserving focus for real threats and reducing alert fatigue across the SOC.
5) Which platforms are best for SMBs and startups?
Prioritize AI-powered cybersecurity tools for SMBs that are easy to deploy, integrate, and scale. Strong contenders for 2025 include: Microsoft Security Copilot (tight M365/Defender integration, copiloted investigations), CrowdStrike Falcon (lightweight EDR/XDR with robust ML detections), Darktrace (self-learning behavioral analytics across email, cloud, OT/IT), and IBM QRadar/Cloud Pak for Security (threat analytics plus orchestration). For lean teams, look for outcome-oriented bundles: email security with NLP phishing defense, EDR/XDR with automated isolation, identity protection with risk-based MFA, and a low-maintenance SIEM/SOAR layer. Favor usage-based pricing, strong defaults, and prebuilt playbooks over heavy customization. Map each tool to a core control: endpoints, identities, email, data, and network; ensure they share telemetry and verdicts. If budget is tight, start with identity/email/endpoint (highest ROI), then layer SIEM/SOAR. The north star: measurable gains in MTTD/MTTR, fewer false positives, and a clear adaptive AI security posture as you grow.
6) What are the ethical risks of deploying AI in cybersecurity?
Key risks span privacy, fairness, and transparency. Behavioral analytics and continuous monitoring can over-collect sensitive data if not bounded by policy. Models may reflect historic biases, unfairly targeting certain users or geographies. To mitigate, anchor on ethical AI deployment in cybersecurity: data minimization, purpose limitation, retention caps, and role-based access; model documentation (data sources, features, known limitations); periodic bias and drift audits; and appeal mechanisms for contested decisions. Preserve human oversight for impactful actions and maintain complete audit logs for compliance (e.g., GDPR/CCPA, sectoral standards). Communicate clearly what telemetry is collected and why—trust rises when employees understand that controls protect data, not surveil arbitrarily. Finally, test fail-safes: can you explain an alert, revert an action, and remediate harm if the model errs? Responsible programs treat AI as a control subject to governance—measured, reviewed, and continuously improved—so speed never comes at the expense of rights or accountability.
7) What impact does AI have on identity management and fraud prevention?
AI modernizes IAM with behavioral biometrics for identity management (typing cadence, pointer dynamics, mobile sensor patterns) and continuous risk scoring across sessions. Low-risk flows remain frictionless; riskier ones trigger step-up verification or re-authentication. On the back end, graph and sequence models flag impossible travel, anomalous privilege use, and session hijacks. For payments and onboarding, AI detects mule behavior and synthetic identities by correlating device fingerprints, document metadata, and transactional histories. Programs often report ~50% reductions in fraud attempts within months as high-risk sessions are challenged earlier. Pair IAM with AI-driven vulnerability management and patching to close identity-related misconfigs (e.g., exposed tokens, stale accounts). For high-assurance use cases, an adaptive AI security posture with blockchain can anchor integrity—immutably recording identity events or verifying artifacts to thwart tampering. Net effect: fewer account takeovers, smoother user experiences, and materially lower fraud losses—delivered by defenses that learn from every authentication and evolve in real time.
