Building Secure Bubble.io Apps: Essential Security Tips
Building Secure Bubble.io Apps: Essential Security Tips
Meta Description: Building secure Bubble.io apps requires attention to data security and user access control. Learn essential security tips to protect your Bubble app and users.
Outline:
Introduction
1. Secure Your Bubble Account and App Access
2. Enable SSL for Encrypted Connections
3. Protect Data with Privacy Rules
4. Encrypt Sensitive Data in Your Database
5. Implement Robust User Authentication (OAuth & SSO)
6. Enforce Strong Passwords and 2FA
7. Apply Role-Based Access Control (RBAC) and Page Restrictions
8. Keep API Keys and Secrets Off the Client
9. Follow API Security Best Practices
10. Use Trusted Plugins and Secure Code
11. Secure Your Workflows and Backend Actions
12. Implement Rate Limiting and Throttling
13. Monitor Activity and Audit Regularly
14. Handle Errors to Avoid Data Leaks
15. Keep Your Bubble App Updated
Conclusion
Introduction
Bubble.io is a powerful no-code platform that enables developers and startups to build web applications quickly, while also allowing for secure app development by following security best practices throughout the app development process. However, with great power comes great responsibility – the ease of Bubble comes with potential security challenges. Building secure Bubble.io apps is crucial not only for protecting sensitive user data but also for maintaining the trust of your users and clients. Fortunately, Bubble provides a strong security foundation (including compliance with SOC 2 Type II standards and data encryption), but as the app creator, you must actively configure and manage security on your end. In other words, Bubble security is a shared responsibility between the platform and you, the builder.
This comprehensive guide presents essential security tips to help you safeguard your Bubble.io application. We’ll cover data security measures, authentication mechanisms, privacy settings, safe plugin usage, and more. By following these best practices, you can fortify your no-code app against vulnerabilities. Cyber attacks are a persistent threat, so proactively addressing them is essential to protect your application and its users. Securing your app might seem daunting, but it’s absolutely achievable. Remember, an ounce of prevention is worth a pound of cure, especially in your app's security. Let’s dive into the key strategies for building a safe and secure Bubble.io app.

1. Secure Your Bubble Account and App Access
The first step in building a secure Bubble app is to lock down the foundation – your Bubble account and app settings. Unauthorized access to your Bubble account would be one of the most severe breaches, since it would grant control over all your applications and data. To prevent this, use a strong, unique password for your Bubble account and enable two-factor authentication (2FA) on your Bubble account login. Bubble offers powerful account security tools such as 2FA to help keep your account safe.
Next, review your application’s settings to restrict access. Bubble provides features to protect your app editor and development versions. For example, you can require a username and password to access the app in Development mode, ensuring that only authorized team members or testers can view your staging app. Be mindful when inviting collaborators to your Bubble app – assign them appropriate roles (like read-only or edit rights). Avoid granting full access to collaborators unless absolutely necessary. Bubble allows you to control collaborator access levels, so take advantage of those settings. Always review and replace default permissions with more restrictive, explicitly defined permissions to prevent unauthorized data exposure.
In short, secure the “keys to the kingdom” first. By protecting your Bubble account and limiting who can access your app’s backend, you lay a safe groundwork. This preventative step will make sure that only trusted individuals can modify your app or view sensitive data during development. It’s much better to start with these protections in place than to regret a breach later. However, remember that no security setup can guarantee complete safety if permissions are not properly managed.
2. Enable SSL for Encrypted Connections
Data security begins with encrypting data in transit. You should always serve your Bubble application over HTTPS (SSL/TLS) so that all information exchanged between users’ browsers and your app is encrypted. Bubble makes this easy – in your app settings, simply check the option to enable SSL for your custom domain. This ensures that anyone intercepting the traffic cannot read sensitive data like login credentials or personal information. In fact, Bubble employs HTTPS encryption to protect all data transmitted between the client and server, but you must make sure your app is correctly configured to use it. Additionally, data in transit is automatically encrypted by Bubble.io, providing a strong baseline of security for your application.
Using SSL is a basic yet critical security step. Always look for the padlock or “https://” in your app’s URL when testing. If your app is on a Bubble subdomain, Bubble provides HTTPS by default; for custom domains, enabling the SSL option will procure an SSL certificate for you automatically. This not only encrypts data in transit but also adds credibility to your application (users have come to expect the padlock symbol for any application handling personal data). In summary, never allow unencrypted HTTP connections to your Bubble app – a secure app starts with a secure connection.
3. Protect Data with Privacy Rules
Bubble’s Privacy Rules are one of your best defenses against data leaks. Privacy rules let you control which users (or roles) can view or modify different types of data in your database. By default, any data in your Bubble database could be accessible if someone knows or guesses the endpoints, unless you define proper privacy rules. As a general rule, there should never be unprotected data unless it’s truly public content (e.g. a public blog post). Setting up a privacy rule on all your non-public data types will ensure that users cannot retrieve data they shouldn’t see.
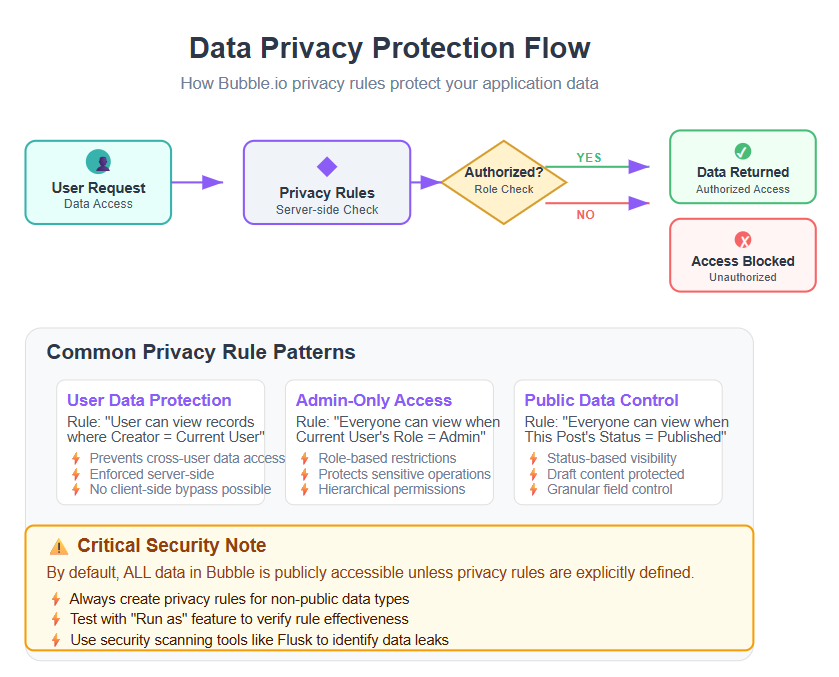
When configuring privacy rules (found under the Data > Privacy tab in the Bubble editor), think through who needs to access each type of data. For example, you may allow users to read their own records but nobody else’s, or only allow admins to modify certain fields. Bubble’s privacy system will enforce these rules on the server side, meaning the server will not even send disallowed data to the user’s device. Be careful not to configure workflows or API endpoints to ignore privacy rules, as this can expose sensitive data. This prevents accidental exposure of sensitive information. Remember that Bubble’s platform considers all data public unless restricted – privacy rules are needed to keep the data safe and avoid accidental leaks.
It’s wise to test your privacy rules thoroughly. Bubble provides a “Run as” feature to view the app as different users, or you can use tools to scan for any data that might be leaking. In fact, security audit tools like Flusk often specifically check for missing privacy rules because data leaks are a common oversight. Design your database structure with privacy in mind as well – for instance, link data to a User account or role so you can easily create rules like “User can view data that they created” or “Admin can view all records.” Make sure that sensitive data is stored securely and only accessible according to privacy rules. By implementing strict privacy rules, you ensure that each user only accesses what they are meant to, keeping private data truly private.
4. Encrypt Sensitive Data in Your Database
Beyond privacy rules, consider encrypting highly sensitive data at the application level. Bubble already stores all database data with encryption at rest on its servers (using AES-256 encryption on AWS RDS), which provides a strong baseline of security. Encryption at rest not only protects confidentiality but also helps maintain the integrity of sensitive data by ensuring its accuracy and trustworthiness within the secure server environment. However, if you have certain information that is extremely sensitive – such as personal identifiers, financial details, or medical data – it’s wise to add an extra layer of protection. In practice, this means encrypting those data fields before they ever reach the database, and decrypting them only when needed (and authorized) on the client side.
For example, rather than storing a user’s Social Security Number or credit card number in plain text in the database, you might encrypt it using a secret key that only your app knows. That way, even if someone somehow bypassed your privacy rules, the data would be unreadable without the decryption key. Bubble’s documentation recommends not storing very sensitive data unencrypted; ideally, offload that responsibility to specialized third-party services like Stripe (for payments) or OAuth providers (for passwords). If you must store it, you should encrypt those values yourself and decrypt them only when needed.
Implementing custom encryption might involve using a Bubble plugin or integrating with an external encryption API. The key point is to ensure that the raw sensitive value is never sitting exposed in your database. For instance, some Bubble developers use encryption plugins to encode data like private messages or API keys. Do note that if you handle encryption/decryption in your app, you’ll need a secure way to manage the keys (and users must not lose their keys or they lose access to the data). While this is an advanced technique, it significantly reduces risk. It’s an example of the principle “don’t put all your eggs in one basket” – even if someone got your database, they still couldn’t get the secrets without the encryption key. Use this approach selectively for data that truly warrants it.
5. Implement Robust User Authentication (OAuth & SSO)
Strong user authentication is the front door to your application’s security. At minimum, Bubble’s built-in email/password login system should be used with care: always use SSL (as discussed) for logins, and consider requiring email verification for new users. Beyond the basics, you can improve authentication security and user convenience by implementing OAuth or Single Sign-On (SSO) options. Bubble makes it possible to let users log in with services like Google, Facebook, or LinkedIn using OAuth 2.0. By offering “Log in with Google/Facebook” for example, you offload the authentication security to those providers – they handle the passwords and multi-factor on their side, and Bubble simply trusts the confirmed identity. This reduces the risk associated with storing and managing user passwords yourself.
For organizations or internal apps, SSO can be a critical feature. You might integrate a corporate SAML or OAuth-based SSO provider so that your app’s login ties into the company’s central identity system. This ensures that if, say, an employee leaves the company, their access to the Bubble app can be revoked centrally. Bubble doesn’t natively support SAML out of the box, but there are plugins and workarounds to integrate such services. The key is to use proven, secure authentication methods rather than any “rolled-your-own” login schemes. Avoid practices like sending plaintext passwords via email or allowing users to choose extremely weak passwords (we’ll address password policies next). Also, ensure your app’s sign-up and login workflows are protected – for instance, don’t expose an endpoint that creates accounts without proper verification or rate limiting.
In summary, make it as easy and secure as possible for users to authenticate. Use battle-tested identity providers when you can, and always transmit credentials securely. A secure authentication system is the gatekeeper preventing unauthorized users from entering your application, so it’s worth investing time to get it right. Combined with the next tip (strong passwords and 2FA), you’ll have a solid authentication setup for your Bubble app.
6. Enforce Strong Passwords and 2FA
Even with a good authentication system in place, you should enforce policies that make user accounts harder to compromise. Bubble allows you to define a password policy in your app settings (under Settings > General) to require a minimum password length and complexity for users. Configure this to require strong passwords – for instance, at least 8 characters with a mix of numbers and uppercase letters (or even longer and including special characters for more security). This prevents users from choosing trivial passwords that attackers could easily guess. Educate your users through UI prompts or onboarding to choose a robust password that they don’t reuse elsewhere.
Additionally, enable two-factor authentication (2FA) for user logins in your app. Bubble’s platform includes built-in support for TOTP (time-based one-time password) 2FA for apps on certain plans (Growth plan and above), and you can set this up to require users to enter a verification code from an app like Google Authenticator when logging in. 2FA dramatically reduces the risk of account takeover, because even if a user’s password is stolen, an attacker would still need the second factor (like the code on the user’s phone) to log in. If your Bubble plan doesn’t support the built-in 2FA feature, you can implement a custom 2FA flow using plugins or external services – for example, sending one-time codes via email or SMS, or using a plugin that integrates with authenticator apps.
The combination of strong password requirements and 2FA provides layered security for user accounts. Also consider other measures: force users to update weak passwords, lock out or throttle login attempts after several failures (to prevent brute force attacks – more on rate limiting later), and remind users not to reuse passwords. By making it harder for attackers to break into an account, you protect not just that user’s data but potentially all users (especially if compromised accounts could be used to social-engineer others). Remember, your app’s security is only as strong as its weakest password, so don’t leave the front door unlocked.
7. Apply Role-Based Access Control (RBAC) and Page Restrictions
Not every user should have access to every feature or data in your app. By implementing Role-Based Access Control (RBAC), you ensure that each user only has the permissions necessary for their role. Start by defining what roles or user levels make sense for your Bubble app – common examples are Admin, Moderator, Standard User, Guest, etc. For each role, determine what actions and data should be accessible. Bubble doesn’t have a built-in role management UI for app users, but you can create a field on the User data type (e.g. a text field or option set for role) and assign roles to users. Then, throughout your app, enforce those roles: show/hide certain elements based on the user’s role, and guard critical workflows or data with role checks. This minimizes the risk of unauthorized access by principle of least privilege – a regular user cannot simply manipulate the app to perform admin-only functions if the app logic consistently checks their role.
In practice, you might have pages or administrative dashboards that only an Admin should reach. You can set up page load workflows that redirect a user away if they lack the required role, or simply not show the navigation to those pages for non-privileged users. However, remember that hiding a page link is not sufficient security by itself – a determined user could guess a URL. That’s why coupling page restrictions with the back-end privacy rules and workflow checks is important. For example, an admin page might list all users’ data; even if a non-admin somehow finds that page, your privacy rules on the User data type should prevent them from actually retrieving any data, and a workflow on page load can kick them out. Essentially, you have multiple layers: UI-level restrictions, workflow conditions, and privacy rules all working together to enforce the role permissions.
Implementing RBAC in Bubble often also involves conditionally running workflows. You can use the “Only when” conditions on actions to ensure, say, a delete operation only executes if Current User’s role is Admin. Test these scenarios with different user roles to ensure there are no gaps. Many common security issues in Bubble apps come from poorly managed user roles or assumptions that certain buttons won’t be clicked by unauthorized users. By explicitly checking roles and restricting pages, you take away those assumptions and positively enforce your security model. In summary, define your user roles clearly and use those roles everywhere necessary (pages, workflows, and privacy rules) to create a robust access control system in your app.

8. Keep API Keys and Secrets Off the Client
A golden rule of web development is to never expose secret keys or sensitive credentials in the client-side (browser) code, and this holds true in Bubble. If your Bubble app integrates with external APIs or services, make sure any API keys, secret tokens, or private credentials are kept server-side. Access tokens should also be securely managed—store them in backend workflows or private parameters, and never expose them in frontend code or URL parameters to prevent unauthorized access. Bubble’s API Connector plugin allows you to mark API keys as Private, which means they will not be sent to the browser. Use that feature for any secret API keys. Alternatively, you can store secrets in backend workflows or in your database (as long as you protect those with privacy rules) so that when calls are made, the secret is added on the server side. The reason is simple: if you put a secret in a Bubble page, a tech-savvy user can inspect the page’s source or use developer tools to find it. Even if you don’t visibly display it, it might be present in the HTML/JSON the app sends. Bubble’s documentation explicitly warns that if you inadvertently place something like an API key in your app pages, users may be able to extract it.
So, how do you call external services securely? If it’s a simple API call from your app to an external service, use the server-side API workflows or the API Connector with authentication. Mark keys as private in the API settings, which ensures the key is substituted on the server. For example, when using a service like Stripe, Bubble’s Stripe plugin and API settings handle the secret keys on the backend – only publishable keys (which are meant for public use) are exposed on the client. When configuring API calls, securely handle parameters such as endpoint URLs and tokens by storing them in backend workflows or private settings, especially when managing different environments (development vs. production). If you need to use a secret on the client (some services have client-side keys that are safe to use), double-check that it’s truly intended to be public. When in doubt, assume it should be kept private.
In cases where you might be tempted to use custom code (like an HTML element or JavaScript) that requires a secret, pause and reconsider. Can you redesign it to avoid exposing the secret? Perhaps call a Bubble backend workflow that returns the needed data instead of directly using the secret in the browser. By keeping secrets off the client side, you thwart a whole class of potential attacks. An external attacker or even a curious user cannot steal what isn’t there. A good practice is to audit your app’s pages for any sensitive information – API keys, database IDs that shouldn’t be public, etc. If you find any, refactor to move them into server-side logic. This practice goes hand-in-hand with the privacy rules: data and secrets stay on the server unless a user is truly authorized to see them.
9. Follow API Security Best Practices
Bubble apps often use APIs – both calling external APIs and exposing their own data via Bubble’s API features. When integrating with other apps and systems, it’s important to secure both incoming and outgoing API communications, manage API keys carefully, and ensure that API connections to other apps do not introduce vulnerabilities. To secure your app, follow standard API security best practices. If you have enabled Bubble’s Data API or Workflow API for your app, ensure that you require proper authentication for those endpoints. Bubble provides options to generate API tokens and to require an API key for requests, which you should use. Do not leave your Bubble API endpoints open to the public unless absolutely necessary, and never expose more data than needed. In fact, if you’re not using certain API features, it’s safest to disable them entirely. Disabling unused API features reduces the attack surface of your app, meaning attackers have fewer entry points to exploit. API interactions can open vulnerabilities if set up incorrectly, so it’s crucial to configure them with security in mind to prevent unauthorized access or data breaches.
For any API workflows you create (these are backend workflows that can be triggered via API), use authentication rules or secret keys in the URL to protect them. For example, if you set up a webhook endpoint, you might include a secret token that the external service must send, and your workflow checks for it before proceeding. This ensures that only legitimate sources can invoke your workflow. When calling external APIs from Bubble, always use HTTPS endpoints (which is usually standard now) so that data isn’t intercepted. Also, be mindful of the data you receive – validate it if necessary (though Bubble will generally handle data types for you, it’s good to think about expected vs actual data to avoid any injection attacks via APIs).
Another aspect is limiting what any given API client can do. For instance, if you provide an API for your app’s data, consider implementing rate limiting (throttling how many requests can be made) and using API keys that have scoped permissions. Bubble’s built-in API can be combined with your privacy rules to ensure data is only returned if the request is authorized. Monitor your API logs for unusual activity, such as bursts of requests or frequent failed calls, which could indicate someone probing your endpoints. Using external API management services or WAF (web application firewall) rules via Cloudflare can add more protection for critical APIs.
In short, treat your app’s APIs with the same care as you do the front-end. Secure them with authentication, least privilege, and by shutting off anything you don’t need. Following these best practices will keep both the data flowing in and out of your app under tight control, making it much harder for an attacker to find a weakness.
10. Use Trusted Plugins and Secure Code
One of Bubble’s strengths is its plugin ecosystem – you can extend your app with community-built plugins for added functionality. But with that flexibility comes some risk. Always be cautious and select only trusted, well-reviewed plugins for your app. A malicious or poorly built plugin could introduce security vulnerabilities. For example, a plugin could potentially include hidden code that steals data or compromises your app, especially if it runs client-side code. As the Canvas/Airdev security guide notes, using community plugins carries inherent risks because a plugin developer could be malicious and try to capture data from any app that installs their plugin. Bubble does not (and realistically cannot) fully vet every piece of code in every third-party plugin, so due diligence falls to you.
Before installing a plugin, read its reviews and documentation. Does the developer seem reputable? Have other users reported security issues? If the plugin is open-source, consider reviewing the code or at least scanning it for anything suspicious. If you only need a small piece of functionality, sometimes it might be safer to build it yourself in Bubble (or with a short JavaScript snippet you can inspect) rather than installing an unknown plugin that significantly alters your app. Also, remove plugins that you no longer use – unused plugins can still pose a risk if left installed (and it reduces bloat in your app).
Similarly, be careful with any custom code you add via the HTML element or Script meta tags. Bubble’s native elements automatically escape user-generated content to prevent issues like Cross-Site Scripting (XSS), but a plugin or custom HTML might not have those protections. For instance, if you display user input inside a plugin element and the plugin doesn’t sanitize it, a clever user could input malicious HTML/JS that runs in other users’ browsers. Additionally, ensure that any files uploaded or managed by plugins are set to private and protected by privacy rules, so sensitive files are not publicly accessible or exposed through insecure workflows. If you do need custom code, make sure to sanitize any data that flows into it, and consider using Bubble’s provided methods (like the :formatted as text to strip HTML, etc.). Essentially, treat custom code as a potential hole in Bubble’s safe garden – patch that hole by writing it securely.
To summarize, extend your Bubble app carefully. Use plugins from credible sources and keep them updated. Avoid those that ask for excessive permissions or that duplicate something Bubble can do natively. And when writing custom code, follow security best practices just as you would in a traditional coding environment. By being selective and careful, you can enjoy Bubble’s extensibility without compromising your app’s safety.
11. Secure Your Workflows and Backend Actions
In Bubble, a lot of the application logic is implemented through workflows. It’s important to design those workflows with security checks so that users cannot abuse them or trigger actions they shouldn’t. One critical concept is deciding what should run on the client side versus the server side. Server-side (backend) workflows are not directly visible or manipulable by end users, so they’re generally safer for sensitive operations. If you have actions like “delete user data” or “change user role”, consider putting those in an API workflow (backend) and calling it only when appropriate, rather than doing it entirely in a page workflow. This way, you can enforce additional authentication or checks on the server. Bubble’s logs also let you audit these backend workflows, which helps in monitoring.
Always use Bubble’s conditional workflow features to your advantage. For any action that modifies important data, add an “Only when” condition that ensures the current user has permission. For example: “When Delete Button is clicked and Current User’s role is Admin” -> delete thing. This is a safety net in case, for some reason, a normal user triggers that workflow (say, by messing with browser dev tools or due to some logic oversight). If the condition is not met, the action simply won’t run. Combined with Privacy Rules that prevent unauthorized data modifications from the server side, these workflow conditions create defense in depth.
Another area to secure is scheduled or recurring workflows. If you schedule API workflows (e.g. nightly data processing or emailing), ensure they don’t accidentally expose data. For instance, if a scheduled workflow sends an email digest to users, make sure each user only gets their own data in the email. Also, double-check any workflows that run on page load or as API endpoints. If a workflow should only run under certain circumstances (like an endpoint only callable by an admin), implement those checks inside the workflow as well as externally.
Finally, protect against workflow abuse by users. If you have a public-facing form that triggers an expensive operation (like sending 100 emails or a complex search), consider adding constraints to prevent spamming. This can be as simple as disabling a button after one click, or using rate limiting techniques (covered soon) to throttle repetitive actions. Robust error handling in workflows is also part of security – for example, if a payment charge fails, don’t expose any sensitive error details to the user, but do log the issue for admin review.
By securing your workflows, you ensure that your app’s behavior remains correct under the hood even if someone tries to use the app in unexpected ways. The goal is to make sure the app does only what it’s supposed to, and nothing more, for every user action. Think of your workflows as the processes in a secure facility – each one should check badges and permissions before proceeding.
12. Implement Rate Limiting and Throttling
To protect your Bubble app from abuse and ensure performance, consider implementing rate limiting for certain actions and API calls. Rate limiting means restricting how often a user (or an IP address) can perform a particular action within a time frame. This is important to prevent things like brute-force attacks on login forms, spamming of forms or database writes, and scraping or denial-of-service attempts via your pages or APIs. Bubble applications have some built-in limits at the platform level (for example, how many workflows can run per minute based on your app’s capacity), but you as the app developer should enforce finer-grained limits where appropriate. Designing efficient rate limiting strategies helps balance security and user experience, ensuring your app remains responsive while protected from abuse.
For instance, for login attempts, you might decide that more than 5 failed logins in 5 minutes should temporarily block that user or IP from further attempts. You can implement this by tracking login attempts in a Thing (e.g., a data type storing IP or user email and attempt timestamps), and then having your login workflow check that before actually logging the user in. Similarly, if you expose an API endpoint, you could count how many times a given API key or user hits it and start rejecting or slowing responses after a threshold. This kind of logic can often be built using Bubble’s workflows plus some creative use of the database to store counts/timestamps.
Another scenario is preventing a single user from overloading your app with expensive actions. Suppose you have a search feature that could potentially strain the database; you might throttle how often the search can be triggered (maybe by disabling the search button for a few seconds after each search or queuing requests). On the Bubble forum, many have implemented solutions like adding a small delay or using custom states to ignore rapid-fire repeated button clicks. These small user-experience tweaks double as security/performance measures.
If implementing your own rate limiting seems complex, you can also leverage external services or tools. For example, Cloudflare (which fronts Bubble apps on custom domains) can be configured with rules to block or challenge clients that make too many requests. But even within Bubble, the principle stands: don’t allow unlimited rapid actions when it’s not necessary. Legitimate users operate at a human pace, most of the time, so a bit of throttling won’t hurt usability but will stop malicious scripts or bots from hammering your app. By controlling the rate of usage, you safeguard your app’s resources and deter attackers who rely on spamming your app with requests.
13. Monitor Activity and Audit Regularly
Security isn’t a one-and-done task – it requires ongoing vigilance. Make it a habit to monitor your app’s activity logs and perform regular security audits. Bubble provides logs for things like user sign-ins, workflows run, and changes made to data. Periodically review these logs for unusual patterns, such as a single user account attempting hundreds of actions in a short period, or repeated errors that might indicate someone probing your app’s defenses. Monitoring these logs helps you identify potential vulnerabilities or suspicious activity early. By catching suspicious behavior early, you can respond (for example, by blocking a user or tightening a rule) before it escalates.
In addition to manual monitoring, consider using automated security scanning tools. There are services specifically designed for Bubble apps, such as Flusk Vault, which examine your project for common vulnerabilities (like data leaks or unsafe configurations). These tools can provide a report of potential issues so you can fix them proactively. Be sure to review audit results in detail to ensure all security gaps are identified and addressed. It’s also beneficial to occasionally conduct penetration tests or hire security professionals to audit your application, especially if your app handles very sensitive data or financial transactions. An external audit might reveal things you overlooked, and it’s best to find and patch those before an attacker does.
Staying updated with Bubble’s own security updates is another part of auditing. Follow Bubble’s announcements (via their blog or forums) for any reported vulnerabilities or new security features. For example, if Bubble releases a new privacy feature or a fix for a security bug, incorporate that into your app quickly. Regular audits ensure that over time, as you add new features or as threats evolve, your app remains locked down. Just as you would service and inspect a physical security system periodically, do the same for your digital one. This continuous improvement mindset demonstrates Experience, Expertise, Authority, and Trustworthiness (E-E-A-T) in your development process – you show that you care about security at every step, which ultimately boosts user trust.
14. Handle Errors to Avoid Data Leaks
How you handle errors in your app can have security implications. A common mistake is to display overly detailed error messages to users, which might inadvertently reveal system information or data. In a secure Bubble app, you should fail gracefully and without exposing sensitive info. For example, if a login attempt fails, a generic message like “Invalid credentials” is better than “User account not found” – the latter might tell an attacker that a particular email is not registered, which is information they could use. Similarly, if an action triggers an error (say an API call fails or a workflow runs into a condition it can’t handle), do not show raw error dumps to the user. Bubble by default won’t show stack traces or anything too technical to end users, but if you ever use the “An unhandled error occurs” event to display something, keep it generic.
On the flip side, log the details of errors for yourself (in the logs or send them to an admin email) so you can debug. But those details should stay in your private logs. You want to avoid giving attackers hints about your system. Detailed error output can be like leaving clues – for instance, an error message that includes a data field name might confirm the existence of that field. This is why it’s often said in security circles: don’t leak information. In Bubble, check your workflows where things could fail (like payment processing, data search, file upload) and make sure any user-facing message is sanitized.
Another aspect is to turn off any debug modes or temporary logging you used during development before going live. Bubble has a “debug_mode=true” URL parameter that you might use while testing; ensure you’re not instructing users to use that, and consider enabling the setting that disables debug_mode for non-admin users on live if available. Also, remove any test pages or admin pages that output raw data. Some developers create hidden admin pages that query data for convenience – if you have those, secure them or disable them in production.
Regularly back up your data (Bubble offers automated backups and even point-in-time recovery on higher plans – know how to use these features). Tailor your backup frequency and retention policies to meet operational or regulatory demand for data security and retention.
In summary, errors will happen – but handle them in a user-friendly yet tight-lipped way. Apologize to the user and maybe log a support ticket, but don’t show them the internals. This keeps your app from accidentally spilling secrets. As a bonus, it also gives a more polished impression; users see that even when things go wrong, their data is not exposed and the app remains professional.
15. Keep Your Bubble App Updated
Last but certainly not least, keep your Bubble application and its components up to date. The tech world is constantly evolving, and security vulnerabilities are regularly discovered in all software platforms. Bubble itself updates its platform and may release new versions of the Bubble engine – whenever possible, upgrade your app to the latest stable Bubble version (you can do this in the Settings when a new version is available) after testing that nothing breaks. These updates often include security improvements or bug fixes. Likewise, update your plugins to their latest versions. Many plugin developers release patches to fix security issues or compatibility with Bubble changes. Failing to apply updates can leave your app exposed to known vulnerabilities that attackers might exploit.
Besides applying updates, maintain good operational security practices. Regularly back up your data (Bubble offers automated backups and even point-in-time recovery on higher plans – know how to use these features). Backups won’t prevent a breach, but they can be a lifesaver if something goes wrong, allowing you to restore data. Also, review your app’s settings periodically – Bubble might introduce new security settings (for example, an option to enforce secure cookies or content security policies). Take advantage of those as they become available.
If your app uses external libraries or custom code, keep those updated as well. For instance, if you included a JavaScript library via HTML element, ensure you’re pulling it from a trusted source and updating it for any security fixes. The same goes for any external services’ API keys – rotate keys if needed, and remove credentials that are no longer used.
By staying current with updates and best practices, you reduce the window of opportunity for attackers. Many attacks prey on outdated software. Showing that your app is well-maintained sends a signal that security is taken seriously. It’s like keeping the locks on your doors well-oiled and replaced if broken. In combination with all the tips above, an updated app will be a harder target for anyone with bad intentions.
Conclusion
Building secure Bubble.io apps may require some effort and diligence, but it is entirely achievable – and it pays off by protecting your users and your business. We’ve covered a broad range of security tips, from data encryption and privacy rules to user authentication, secure workflows, and more. The overarching theme is that security must be considered at every level of your application. As a Bubble developer, adopting a security-first mindset will guide you to make the right decisions (like using privacy rules, checking roles, and avoiding shortcuts that expose data).
Remember that Bubble itself is invested in security: the platform includes encryption, compliance certifications, and tools for you to use. By combining Bubble’s built-in protections with the best practices outlined here, you can achieve a level of security comparable to traditionally coded applications. Always keep learning and stay vigilant – new threats can emerge, but if you stay informed (for example, by reading Bubble’s updates or security forums) and continuously improve your app, you’ll stay one step ahead.
In the end, a secure app means peace of mind for you and trust for your users. A well-secured Bubble app can be the foundation of a successful product or startup, because users will feel confident using it. So implement these essential security tips, test your defenses, and don’t hesitate to seek expert help or use automated tools for extra assurance. With a robust security posture, you can fully enjoy Bubble’s no-code power – without the worry of unwanted surprises. Happy Bubble building, and stay secure!
