PCI Compliance Made Simple: Integrating PCI Vault with Bubble.io
PCI Compliance Made Simple: Integrating PCI Vault with Bubble.io (Ultimate Guide)
Meta Description: Worried about handling credit card data on Bubble.io? This ultimate guide on “PCI Compliance Made Simple: Integrating PCI Vault with Bubble.io” breaks down 7 easy steps to secure your app with tokenization. Achieve PCI compliance, protect customer data, and build trust – all without coding headaches.
Introduction – Introduce the importance of protecting payment data and achieving PCI compliance in modern web applications. Highlight how PCI Compliance Made Simple: Integrating PCI Vault with Bubble.io is a practical solution for Bubble.io developers.
Understanding PCI DSS – Define what PCI DSS (Payment Card Industry Data Security Standard) is and outline its core purpose in safeguarding credit card information.
Why PCI Compliance Matters – Explain the stakes of handling payment data. Discuss the risks of non-compliance (data breaches, fines, loss of customer trust) with supporting stats (e.g. average cost of data breaches).
Challenges of PCI Compliance for Web Apps – Explore why meeting PCI requirements is challenging, especially for small businesses or no-code apps. Note the complexities of securely collecting, storing, and transmitting card data.
Overview of Bubble.io – Briefly introduce Bubble.io as a no-code platform. Discuss how Bubble empowers app creation but also how it handles data storage by default.
Bubble.io and Sensitive Data Concerns – Address the fact that Bubble apps are not PCI compliant out-of-the-box. Explain why Bubble’s built-in database and workflows shouldn’t directly handle raw credit card details.
What is PCI Vault? – Introduce PCI Vault as a secure, external credit card tokenization service. Mention that it provides a PCI DSS compliant environment to store card data on behalf of your app.
How PCI Vault Works (Tokenization) – Explain the concept of tokenization: replacing sensitive card data with a secure token. Compare tokenization vs encryption (tokens are irreversible references, unlike encrypted data). Outline how PCI Vault’s tokenization process operates with keys, passphrases, and API calls.
Benefits of Integrating PCI Vault with Bubble.io – Highlight advantages:
- Simplified Compliance – Drastically reduce your app’s PCI scope (potentially down to a simple SAQ self-assessment).
- Enhanced Security – No sensitive card data stored in Bubble, lowering breach risk.
- Customer Trust – Show users you take data security seriously, improving reputation.
- Developer Convenience – Avoid building complex security from scratch; use proven vault APIs.
Preparing to Integrate PCI Vault – Outline prerequisites and planning:
- Create a PCI Vault Account – Sign up and obtain API credentials.
- Bubble Setup – Ensure you have the Bubble API Connector plugin ready.
- Identify Data Flows – Determine where in your Bubble app you will capture payment info and need tokenization.
Step-by-Step Integration Guide (7 Steps) – Detailed walkthrough to implement PCI Vault in a Bubble app:
- Step 1: Set Up PCI Vault Account & API Key – Register for PCI Vault and generate your API key (for authenticating requests).
- Step 2: Identify What Data to Tokenize – Decide which inputs (credit card numbers, CVV, etc.) will be securely tokenized and where in your Bubble workflows this will occur.
- Step 3: Create an Encryption Key in PCI Vault – Use PCI Vault’s API to create an encryption key and secure passphrase, which will be used for tokenization and later decryption.
- Step 4: Configure Bubble API Calls for Tokenization – In Bubble’s API Connector, set up calls to PCI Vault’s Encrypt/Tokenize endpoint. Send the sensitive data (card info) along with the encryption key; receive a token in response.
- Step 5: Store the Token in Bubble – Save the returned token (not the raw card data) in your Bubble database. This token represents the card securely.
- Step 6: Retrieve and Use Tokenized Data – When needed (e.g. to process a payment or display last4 digits), call PCI Vault’s Decrypt endpoint with the token and key passphrase. Use the retrieved data as required, without storing it in Bubble permanently.
- Step 7: Test and Secure Your Integration – Thoroughly test the workflow end-to-end. Implement security best practices: enforce role-based access controls, log access to tokens, and handle errors (e.g. expired tokens) gracefully.
Post-Integration Security Best Practices – Additional measures to maintain security and compliance:
- Access Control – Limit who in your team or which parts of your app can initiate decryption (protect keys and passphrases).
- Audit Logging – Keep logs of tokenization and decryption events for monitoring and auditing.
- Error Handling & Alerts – Set up alerts for any failed tokenization attempts or suspicious activity.
- Data Retention Policies – Decide how long tokens should be kept and purge any that are no longer needed.
Maintaining PCI Compliance Over Time – Explain that compliance is ongoing:
- Key Rotation – Periodically rotate encryption keys and update tokens as needed.
- Software Updates – Keep Bubble plugins, API calls, and PCI Vault integrations up to date with the latest security patches.
- PCI Audits/SAQ – If required, annually validate compliance (often just a Self-Assessment Questionnaire when using a vault service).
- Employee Training – Ensure anyone handling the system knows how to do so securely and is aware of policies.
Real-World Example – Provide a hypothetical scenario of a Bubble app (e.g. an e-commerce store or subscription service) using PCI Vault:
- Describe how the app collects payment info via a secure form, PCI Vault tokenizes the card, and the Bubble app stores only the token. The business can charge the customer by sending the token to a payment processor, all without touching raw card data – a win-win for security and ease.
Frequently Asked Questions (FAQs) – Address common queries:
- Q1: Can I use PCI Vault with any Bubble plan or do I need a dedicated server? – A: PCI Vault works via API calls, so it can be used on any Bubble plan that allows external API integration.
- Q2: Does integrating PCI Vault make my Bubble app fully PCI DSS compliant? – A: It significantly reduces your compliance burden by outsourcing sensitive data handling. You’ll likely fall under a simpler compliance category, but you should still follow best practices and possibly fill out a PCI SAQ.
- Q3: Are there alternatives to PCI Vault for Bubble apps? – A: Yes, other services like Basis Theory or Very Good Security provide data vaults and tokenization. Some developers also use payment provider tokenization (e.g. Stripe) if it fits the use case.
- Q4: How is PCI Vault different from just using Stripe or PayPal? – A: Payment processors like Stripe tokenizes cards for use within their system. PCI Vault gives you a neutral vault where you can store tokens and use card data across any processor or for custom workflows, offering more flexibility.
- Q5: Will using PCI Vault slow down my app? – A: The API calls to PCI Vault are lightweight and designed for speed. Any slight overhead is negligible compared to the benefit of security. Properly handled, users won’t notice any delay during form submission.
- Q6: What happens if PCI Vault’s service is unavailable? – A: As with any critical service, PCI Vault likely has high availability and redundancy. It’s wise to build retry logic for API calls (e.g., if a tokenization request fails, try again) and have customer-friendly error messages in place.
Conclusion – Summarize how integrating PCI Vault with Bubble.io makes PCI compliance simple and achievable. Reinforce that by using tokenization, Bubble developers get the best of both worlds: the ease of no-code development and enterprise-grade security. Encourage readers to take action towards securing their Bubble apps and reassure them that with tools like PCI Vault, handling sensitive payment data can be secure, straightforward, and stress-free.
Introduction
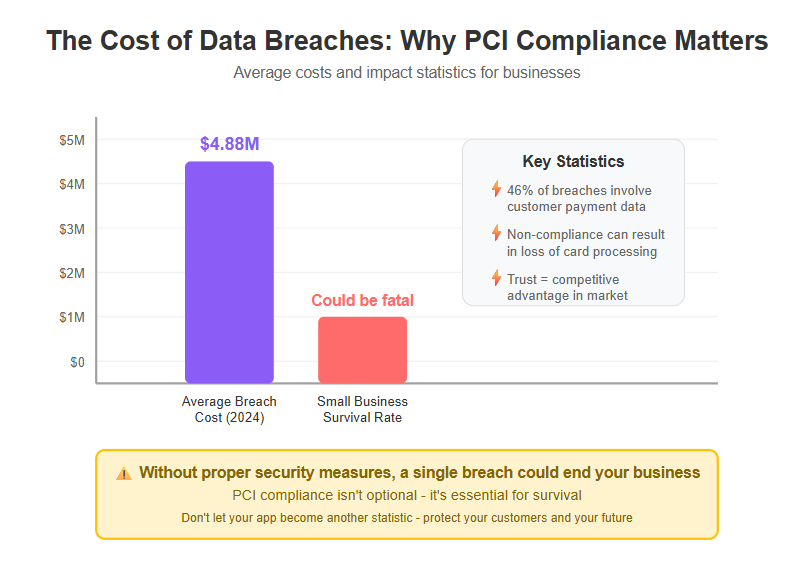
In today’s digital world, protecting payment data isn’t just good practice – it’s absolutely critical. High-profile data breaches and strict regulations have put pressure on businesses of all sizes to safeguard credit card information. As a business owner, you are responsible for ensuring that all critical information, such as payment and customer data, is protected and that your operations remain compliant with industry standards. In fact, the average cost of a data breach hit $4.88 million in 2024, a figure that could sink a small business. This is where PCI compliance comes into play. Achieving compliance with the Payment Card Industry Data Security Standard (PCI DSS) helps you avoid devastating breaches, fines, and reputational damage. However, for many web app builders – especially those using no-code platforms like Bubble.io – navigating PCI requirements can feel like finding a needle in a haystack. The good news? PCI compliance can be made simple by integrating the right tools. In this guide, we’ll show you how Integrating PCI Vault with Bubble.io offers a straightforward path to secure your app and win customer trust. It’s a win-win: you get to focus on building a great application, and your users get peace of mind knowing their credit card data is safe.
Understanding PCI DSS
Let’s start with the basics: What is PCI DSS? PCI DSS stands for Payment Card Industry Data Security Standard. It is a set of security requirements established by major credit card companies (Visa, MasterCard, American Express, etc.) to ensure all businesses that process, store, or transmit credit card information do so in a secure environment. PCI DSS is specifically designed to ensure the safe handling of PCI data, such as credit card numbers and related sensitive information, in accordance with strict security standards. In simpler terms, PCI DSS is like a rulebook for keeping cardholder data safe from prying eyes. These rules cover everything from how you build and secure your networks, to how you protect card data, to maintaining policies and training for your staff. If your app handles credit or debit card information, compliance with PCI DSS isn’t optional – it’s mandatory.
Importantly, PCI DSS compliance isn’t a one-time checkbox. Businesses must regularly demonstrate they meet the standards. Depending on your volume of transactions, you might need annual audits by authorized assessors or at least fill out a Self-Assessment Questionnaire (SAQ). The goal is to ensure that wherever card data flows, robust safeguards are in place. Performing regular security audits helps identify vulnerabilities in payment processing systems, ensuring that any potential weaknesses are addressed promptly. By understanding PCI DSS at a high level, you’re already on the right track. Next, let’s talk about why this matters so much for you and your users.
Why PCI Compliance Matters
Handling customers’ payment information is a bit like holding a live grenade – you must be extremely careful or risk catastrophic consequences. PCI compliance matters because it protects both your customers and your business. Imagine the fallout if your app accidentally leaked credit card details: customers would face fraud, you’d face fines or lawsuits, and your reputation could be shattered overnight. Indeed, nearly 46% of breaches involve customer personal data like payment details, and the financial repercussions can be huge. Non-compliance with PCI standards can result in steep fines from banks, legal penalties, or even losing the ability to process cards at all. In short, failing to secure card data isn’t just bad for users – it can quickly put you out of business. Identifying potential threats to payment data, such as security vulnerabilities or configuration mistakes, is essential to proactively safeguard your application.
On the flip side, getting PCI compliant offers positive benefits. It shows you take data security seriously, which can be a selling point for customers and partners. In a competitive market, trust is everything. When users see that you’ve implemented solid security measures, such as tokenization via PCI Vault, it gives them confidence to use your service. Compliance can also streamline your operations by forcing you to follow security best practices that reduce the chance of incidents. Having an incident response plan in place ensures your team can address security breaches efficiently and assign responsibilities for swift action. Staff training improves awareness of security risks among team members, ensuring everyone is equipped to handle sensitive data securely. It’s like reinforcing the foundation of your house to withstand storms – a bit of effort up front saves a ton of trouble down the road. Now that we know why it’s vital, let’s address why achieving compliance can be challenging, especially for modern web apps.
Challenges of PCI Compliance for Web Apps
Traditional enterprises often have dedicated security teams and budgets to handle PCI compliance. But what if you’re a solo developer or a startup building a web app on a platform like Bubble.io? The challenges of PCI compliance can seem overwhelming. No code tools have transformed the landscape of software development, enabling non-developers to build powerful apps quickly, but they also introduce new compliance challenges that must be addressed. Compliance processes focus heavily on infrastructure and code management, which are managed differently in no-code platforms like Bubble.io. PCI DSS has around 12 major requirements (and numerous sub-requirements) covering areas from network security to access controls to regular monitoring. For a small team, implementing all these controls is no walk in the park. It’s not just about writing secure code – it’s about secure infrastructure, continuous audits, and documenting everything. Web applications, by nature, are exposed to the internet and thus constantly targeted by attackers. If you’re not extremely careful in how you collect and store card data, you could inadvertently open a door to hackers.
One major challenge is securely handling credit card input. The moment card data enters your system, it’s in scope for PCI compliance. That means every system component it touches (front-end, back-end, database, logs, etc.) must meet stringent standards. For many developers, the safest route is to avoid handling raw card data altogether – but how can you process payments then? Often, businesses rely on third-party payment processors (like Stripe, PayPal, etc.) so that the sensitive data never hits their servers. This is a smart strategy, but it can be limiting if you need to store card details for later use or want more control over payment data. Without a specialized solution, achieving PCI compliance on your own would require encryption, firewalls, intrusion detection systems, secure networks, constant updates – the whole nine yards. As one Bubble forum user wisely noted, “There’s a lot that goes into being PCI compliant from how you collect the data and where it’s stored to how it’s accessed and displayed.” For small teams, choosing the right no code tool can simplify some aspects of PCI compliance by providing built-in security features and compliance support. In short, it’s a heavy lift for an indie app creator.
So, what’s the alternative? How can you as a Bubble.io developer meet these security demands without reinventing the wheel? The answer lies in shifting the hardest parts of compliance to a specialized service – and that’s exactly where PCI Vault comes in.
Overview of Bubble.io
Before diving into PCI Vault, let’s briefly talk about Bubble.io. If you’re new to it, the Bubble platform is a popular no-code platform that empowers people to build web applications through a visual interface, without traditional programming. It’s like the Swiss Army knife of app development – Bubble handles the heavy lifting (like database, server, and front-end rendering) so you can focus on design and functionality. With Bubble, entrepreneurs and makers can quickly spin up everything from simple prototypes to full-fledged marketplaces. Additionally, Bubble has a robust plugin ecosystem that supports complex application design, enabling developers to extend functionality and integrate with various third-party services seamlessly.
However, with great power comes great responsibility – especially regarding data. Bubble provides a built-in database where you can store user information, and workflows that allow your app to send data to external services or vice versa. By default, Bubble apps communicate over HTTPS (secure web protocols) and the platform itself has decent security for general data. But when it comes to extremely sensitive data (like credit card numbers or personal IDs), Bubble’s ease-of-use could become a double-edged sword. If a developer isn’t careful, they might inadvertently store sensitive info in plaintext or expose it through logs or browser workflows, simply because the platform makes data handling so straightforward. It’s also crucial to properly manage API access and security within your app's code, even when using a no-code solution like Bubble, to prevent vulnerabilities and protect sensitive data. Bubble uses HTTPS encryption to ensure all data transmitted between the browser and Bubble's servers is secure. Bubble does offer integrations with payment services like Stripe out-of-the-box (through plugins), which is their recommended approach for transactions – these keep card data away from Bubble’s own database. Still, more complex use cases might require handling payment data differently, which Bubble alone isn’t designed for.
In summary, Bubble.io is fantastic for rapid development and can handle a lot of app logic, but it doesn’t inherently provide PCI compliance or specialized security measures for protecting credit card data. You wouldn’t expect it to – after all, PCI compliance is not a trivial feature. Next, we will see why a Bubble.io app needs some help to handle payments securely and how PCI Vault fits into the picture.
Bubble.io and Sensitive Data Concerns
So, is Bubble.io PCI compliant by itself? The short answer is no – Bubble apps are typically not PCI compliant out-of-the-box. This means if you collect credit card numbers directly through a Bubble form and store them in Bubble’s database, you’d be violating PCI DSS guidelines (unless you’ve somehow put Bubble through a rigorous compliance audit, which is impractical for most). Bubble’s platform has not been certified as a PCI-compliant environment for storing untokenized cardholder data. And it’s not just about storage – even transmitting card data through Bubble’s servers, or processing it in workflows, could bring your app into PCI scope. Essentially, the moment raw card data enters your Bubble app, you’re responsible for a whole laundry list of security measures.
Some of the specific concerns include:
- Database Security: Bubble’s default database is not certified for storing credit card numbers in the clear. Specific data, such as credit card numbers or other sensitive payment information, must be safely stored in a PCI-compliant environment rather than Bubble’s default database. You would need strong encryption and access controls beyond what Bubble provides by default.
- Server Logs and Debugging: Bubble may log requests and workflows for debugging. If card data is passed in those requests (say via API connector or as form data), it might end up in logs – a big no-no for PCI.
- Unauthorized Access: Without strict controls, any admin or developer with access to your Bubble app editor could potentially see stored data. PCI requires limiting access to card data on a need-to-know basis.
- Lack of Audit Trail: Bubble doesn’t automatically provide a detailed audit trail of who accessed sensitive data when, which is something you’d want for forensic and compliance reasons.
Given these issues, Bubble developers typically avoid directly handling credit cards. The common practice is to use payment plugins (like Stripe) that handle the card input in a secure popup or redirect to a hosted form. That way, the card info bypasses Bubble entirely and you get back a token or payment confirmation. But if your project requirements mean you do need to collect and store payment data (for example, to charge customers later or use a payment gateway not supported by a simple plugin), you’ll need a different approach. That’s where an external PCI-compliant vault becomes your best friend. Let’s introduce one such solution: PCI Vault.
What is PCI Vault?
Picture a high-security vault in a bank: inside, sensitive valuables (in this case, credit card details) are locked away, and only authorized people with the right keys can access them. PCI Vault functions just like that, but in the digital realm. It is a specialized service designed to securely capture, tokenize, and store credit card data on behalf of your application. In other words, instead of your Bubble app storing a customer’s card number, PCI Vault will store it in its PCI DSS-compliant environment, and give you back a harmless placeholder (a token).
PCI Vault is often described as a Credit Card Tokenization Storage Provider. Its key features include secure tokenization, robust compliance management, and strong encryption to protect sensitive data. It’s vendor-neutral, meaning you can use those tokens with any payment processor or system you want – you’re not locked into a specific gateway. PCI Vault also offers unified APIs, enabling seamless integration with various payment processors and simplifying secure data handling across multiple services. By using PCI Vault, you essentially shift the burden of PCI compliance for card storage and processing to that service. Your Bubble app never directly sees the raw card data, so your app’s PCI scope is greatly reduced. In fact, many times using such a vault can reduce your obligations to just an annual SAQ (Self-Assessment Questionnaire) instead of undergoing complex audits. It’s akin to outsourcing the hardest part of security to experts who do it at scale.
From a developer’s perspective, PCI Vault provides APIs and possibly front-end components to interact with. For example, there might be an API endpoint to send card data for tokenization, another to retrieve (decrypt) it when needed, and so on. The service will enforce that all communication is secure (using encryption, TLS, etc.), and it may require authentication like API keys and encryption keys or passphrases for extra safety.
To sum up, PCI Vault is the solution that makes PCI compliance simple for Bubble apps: it handles the heavy lifting of security. Now, let’s dive deeper into how PCI Vault actually works, particularly the concept of tokenization which is at its core.
How PCI Vault Works (Tokenization)
Tokenization is the magic that powers PCI Vault. If you’re not familiar with the term, tokenization is the process of replacing sensitive data (like a credit card number) with a non-sensitive equivalent (a token). The token is usually a randomly generated string of characters that has no meaningful value if stolen – it’s essentially an alias. Only the token vault (PCI Vault, in our case) can map that token back to the original card details, and it will only do so under strict conditions.
Here’s a simple way to think about it: Imagine you have a secret message written on paper. Instead of carrying the original message around (risking it might be read by someone else), you lock the message in a secure box at a bank vault. The bank gives you a claim check – a random number that references your box. That claim check is useless to anyone who finds it on the street, because without the bank’s authorization and key, they can’t get your message. In this analogy, the secret message is the credit card data, the bank vault is PCI Vault, and the claim check is the token.
Let’s break down how PCI Vault’s tokenization process works in a Bubble integration context:
- Secure Data Capture: When your Bubble app needs to get a credit card from a user, you’ll actually send that data straight to PCI Vault (usually via a secure API call or a provided web component). The card data can be encrypted in transit; PCI Vault expects it to be protected, often using an encryption key that you generate on their system. It is crucial to configure secure API authentication for these API calls to ensure that only authorized requests can transmit sensitive data, further protecting your users' information.
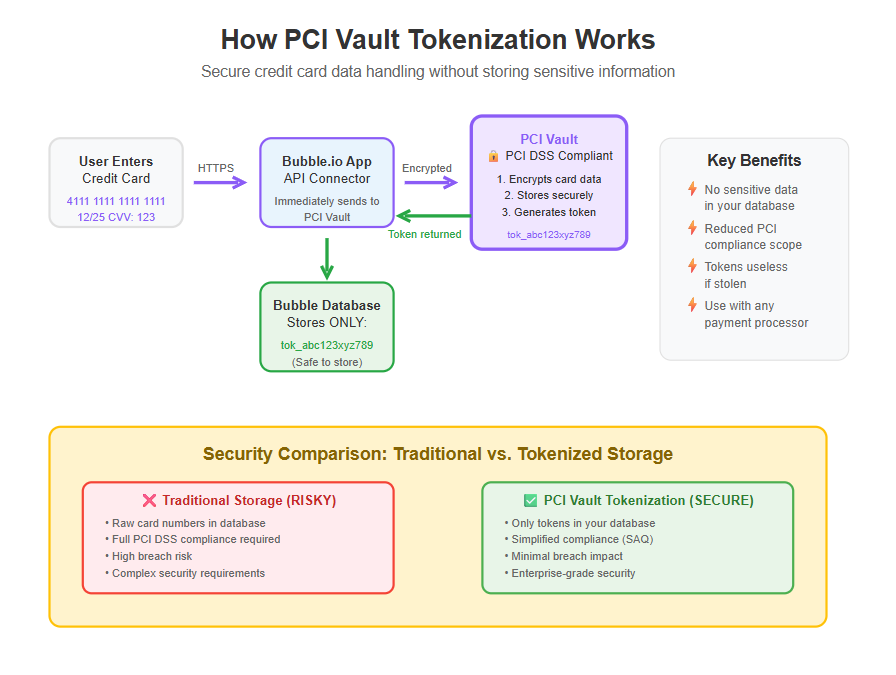
- Token Generation: PCI Vault receives the card data and stores it securely in their system (which is built according to PCI DSS requirements). It then creates a unique token ID that represents that card. For example, a card number 4111 1111 1111 1111 might turn into a token like tok_9a8b7c6d… – a random string.
- Return Token to Application: That token is sent back to your Bubble application. Now your app can store this token safely in its own database. The token by itself is meaningless to any thief; it’s not derived from the card number via a reversible algorithm (unlike encryption, which could be decrypted with the key). It’s a one-to-one reference, like a coat check ticket.
- Using the Token: Whenever your app needs to perform an action that requires the actual card (e.g., charge the card, or display the full number to an admin for some reason), it doesn’t use the card number directly. Instead, it sends a request to PCI Vault like, “Hey, can you please give me the card info for token X?” Of course, this request must be authenticated – typically you’d provide your API key and also decrypt it using the encryption key’s passphrase you set earlier. If everything checks out, PCI Vault returns the needed info (either sending it to a designated secure endpoint or just confirming a payment). When managing encryption keys and passphrases, always use strong passwords for all credentials and secrets to prevent unauthorized access and strengthen your overall security posture.
- Temporary Access and Deletion: A strong design is that PCI Vault might only give you the info through a controlled channel or even a one-time access link. In some implementations, the token might be single-use or you can configure it to expire. The Rapid Developers’ guide mentions a flow where PCI Vault provides a URL/secret that a third-party (like your payment processor) can use once to retrieve the data, and then that endpoint self-destructs. This ensures the sensitive data isn’t lingering around.
It’s worth noting the difference between tokenization and encryption here. Encryption scrambles data with a key, but if an attacker gets the encrypted data and the key, they could decipher it. Tokenization, as done by PCI Vault, completely removes the original data from your app’s environment. Even if someone breaches your Bubble database, they’ll only find tokens – which are useless without access to PCI Vault. This is an added layer of security for your Bubble.io app because it eliminates direct storage of sensitive info.
In summary, PCI Vault works by turning your customers’ credit card info into harmless tokens that you can safely handle. It’s the ultimate example of “what you don’t have, can’t be stolen.” Now, let’s enumerate the concrete benefits you gain by integrating PCI Vault with Bubble.io, beyond the obvious security boost.
Benefits of Integrating PCI Vault with Bubble.io
Bringing PCI Vault into your Bubble app architecture offers a host of benefits that extend across security, compliance, and even business reputation. Here are some of the key advantages:
- ✅ Simplified PCI Compliance: Perhaps the biggest benefit is that your app’s PCI compliance burden drops dramatically. Since PCI Vault is a PCI DSS certified environment, your Bubble app doesn’t have to be one. By using PCI Vault’s tokenization, you may only need to fill out a simpler PCI Self-Assessment Questionnaire (SAQ) instead of undergoing audits. Essentially, you’re outsourcing the hardest part of compliance (storing and securing card data) to PCI Vault. This can save you countless hours of paperwork and potentially thousands of dollars in audit costs. It’s compliance made simple – exactly as our title suggests!
- 🔒 Enhanced Security: Storing credit card data is like guarding treasure – it makes you a target. By not storing it at all (and keeping it in PCI Vault instead), you greatly reduce your risk of data breaches. Even if your Bubble app gets hacked, the attackers can’t grab card numbers because those aren’t there. This reduces the impact of any breach on your system. Also, PCI Vault likely has advanced security measures (encryption, intrusion detection, regular pen testing) in place that would be burdensome to implement on your own. You’re effectively leveraging a security team’s expertise by using their service.
- 🤝 Improved Customer Trust: Today’s consumers are rightfully anxious about how their data is handled. By integrating a secure solution and being transparent (you could even mention in your privacy/security page that “we use a PCI-compliant vault to store all payment info”), you signal to users that you take their safety seriously. This builds trust and confidence, which can be a deciding factor for someone choosing your service over a competitor. Trust isn’t just good karma – it’s good business. Customers who trust you with their data are more likely to complete purchases and become repeat clients.
- ⚙️ Developer Convenience and Flexibility: Using PCI Vault saves you from reinventing the wheel. Implementing strong encryption, secure storage, and compliance checks by yourself would be a massive project. Instead, with a few API calls and settings, you get a ready-made solution. Many vault services, PCI Vault included, provide clear documentation and support. They might even offer client libraries or plugins to integrate easily. This frees you to focus on your app’s core features rather than low-level security protocols. Moreover, because the vault is neutral, you have flexibility. For example, you can tokenize a card once and then use that token to process payments with multiple providers (say, charge through Stripe, and later maybe via PayPal or a bank API) without asking the user for their card again. The data is yours (stored in the vault) and portable wherever you need, which is a level of flexibility pure processor-based tokenization might not give.
- 🚀 Scalability and Future-Proofing: As your app grows, compliance requirements can change or become more demanding. By leaning on a dedicated service that stays up-to-date with PCI rules, you automatically stay current. If PCI DSS standards evolve (they do periodically – e.g., new versions come out addressing emerging threats), PCI Vault will handle those changes in their environment. So you’re always on the cutting edge of compliance without doing the heavy lifting. Additionally, vault services are built to handle high volumes of secure transactions, so you can scale your user base without worrying about outgrowing your homemade security solution.
In short, integrating PCI Vault with Bubble.io gives you the best of both worlds – the agility of a no-code platform with the robust security of a specialized compliance solution. Now that you’re convinced of the benefits, let’s get into the meat of this guide: how to actually integrate PCI Vault with your Bubble app, step by step.
Preparing to Integrate PCI Vault with Your Bubble App
Before jumping into the integration steps, it’s important to get everything in order. Think of this as a pre-flight checklist to ensure a smooth process. Here’s how to prepare:
1. Set Up Your PCI Vault Account: Head over to the PCI Vault website (the official site) and register for an account if you haven’t already. You may need to choose a plan that fits your usage (some services offer free tiers for development and paid plans for production). Once you have an account, navigate to the dashboard or developer settings to generate your API credentials. Typically, this includes an API key (and possibly a secret key). These credentials will allow your Bubble app to authenticate with PCI Vault’s API. Store them securely! Treat API keys like passwords – don’t expose them publicly. Many developers use Bubble’s built-in capability to store API keys in protected fields (like environment variables or the plugin settings that aren’t visible to users).
2. Read the Documentation: It might sound obvious, but reading PCI Vault’s docs can save you a lot of time. Look for a “Getting Started” or “Bubble integration” guide. The docs will detail the required API endpoints, parameters, and any SDKs or plugins available. For instance, find out the endpoints for creating an encryption key, tokenizing data, and decrypting data. Knowing these in advance helps structure your Bubble workflows properly.
3. Install/Enable Bubble’s API Connector: In your Bubble.io editor, ensure you have the API Connector plugin installed (it’s a free official plugin by Bubble). This plugin lets your Bubble app communicate with external APIs. If PCI Vault (or a community developer) offers a ready-made Bubble plugin, you could consider that as well, but using the API Connector is a straightforward and transparent way to integrate. Go ahead and add a new API in the connector, maybe call it “PCI Vault API”, and prepare to configure calls (we’ll do that in the steps).
4. Identify Data Collection Points: Plan where you will collect the credit card information in your app. For example, is it during a checkout form, a subscription sign-up, or an admin entering data for a customer? Create the necessary Bubble input fields for card details (card number, expiration date, CVV, cardholder name, etc.) but be careful with how you use them. You might not want to use regular Bubble input elements for card number if you aim to never expose that data to Bubble’s environment. Some integrations instead use an HTML element or iFrame that directly posts to the vault (we’ll touch on that). However, to keep it simple, initially plan as if you will gather the input and immediately send to PCI Vault via API.
5. Plan Your Workflows: Decide how the tokenization workflow will run. A typical flow might be:
- User enters card info in a form.
- User clicks “Submit” or “Save Card”.
- Bubble workflow triggers an API call to PCI Vault (sending card data and encryption key info).
- PCI Vault returns a token.
- Bubble workflow receives the token and saves it in the database (maybe in a “Customer” data type or “PaymentMethod” thing).
- (Optionally) Bubble then uses that token to perform an action, like initiating a charge via a payment processor, or confirms to the user that their card is saved securely.
Make sure to create a field in your Bubble database to store the token (e.g., a text field called “card_token” under the User or a Payment Method object).
By checking off these preparation steps, you set yourself up for a successful integration. Now, roll up your sleeves – it’s time for the step-by-step implementation guide.
Step-by-Step Integration Guide: PCI Vault + Bubble.io
Now we get to the heart of the matter: integrating PCI Vault with your Bubble.io app. We’ll walk through 7 key steps to get everything working securely. This may look lengthy, but each step is quite manageable. Let’s dive in.
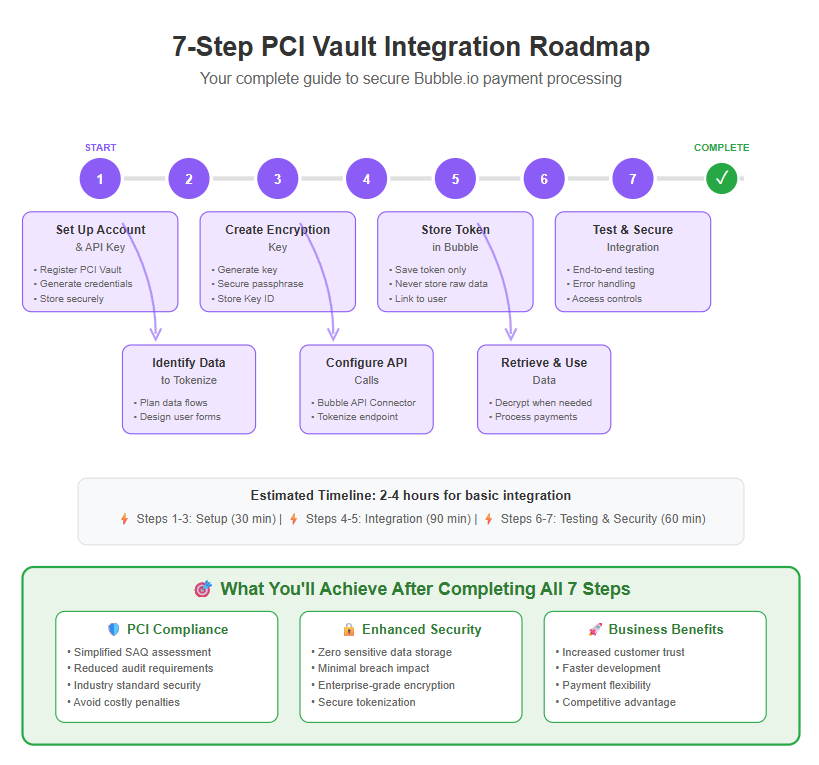
Step 1: Set Up Your PCI Vault Account and API Key
First things first – you need to have access to PCI Vault’s services:
- Register an Account: If you haven’t done so, create an account on the PCI Vault platform. Use a strong password and enable any two-factor authentication offered, as this account will govern access to sensitive operations.
- Obtain API Credentials: Once logged in, navigate to the dashboard or developer settings where you can create API credentials. Typically you’ll generate an API key (public identifier) and an API secret (like a password). For example, you might see a string like pk_live_xxx... for a public key and sk_live_xxx... for a secret key, or some variation. Copy these keys.
- Store Credentials Securely: In your Bubble app, go to Settings → API (or Plugins → API Connector) and add the credentials. If using the API Connector plugin, you can initialize the calls with the key embedded (like in headers), but it’s better to use Bubble’s secrets management. Bubble allows you to store keys in the plugin settings or use environment variables so they aren’t exposed on the front-end. Ensure the API secret is kept confidential – never expose it in client-side code or design.
This step lays the groundwork by giving your Bubble app the “identity” it needs to communicate with PCI Vault. Without valid API keys, PCI Vault will simply reject any requests.
Step 2: Identify Data to Tokenize and Workflow Integration Points
Before you write any integration code (or workflows in Bubble’s case), clarify what data you need to tokenize and when:
- Choose the Data Fields: Typically, you’ll tokenize Primary Account Numbers (PANs) – i.e., the credit card number. You might also tokenize other sensitive fields like CVV or bank account numbers if needed. Write down the list of fields you plan to send to PCI Vault. (Note: PCI Vault might only need the PAN; CVV codes usually should not be stored at all even tokenized, per PCI rules. Often CVV is used once for verification and then discarded.)
- Plan the User Experience: Decide at what point in your app you’ll collect the card info. Common scenarios include during a checkout flow (“Add Payment Method”) or in a user settings page (“Save your card for future use”). Ensure you have a form ready in Bubble for this. Keep the UI user-friendly: clearly label the fields, and maybe add input masking (Bubble can mask inputs like credit card number into groups of 4 digits).
- Workflow Point: For each scenario, plan a workflow event like “When Save Card button is clicked”. In that workflow, you will later add an action to call the PCI Vault API (via the connector).
- Consider Using Vault’s UI Elements: Check PCI Vault’s documentation to see if they offer any front-end components or forms. Some vault providers have a ready-made secure card input form (for example, a JavaScript widget or an iframe) that you can embed in Bubble using an HTML element. This would allow the card data to go directly to PCI Vault from the user’s browser, bypassing Bubble servers entirely (which is even more secure). The WordPress plugin for PCI Vault, for instance, uses a shortcode that loads PCI Vault’s own hosted card form. If something similar exists for Bubble (or generally via a JS library), consider using it. It might complicate the setup slightly but yields maximum security. For our guide, we’ll proceed with the API approach, but keep this in mind as an option.
By the end of step 2, you should know exactly which data you’re tokenizing and have your Bubble form and workflow trigger laid out. This clarity will make the implementation much smoother.
Step 3: Create and Secure an Encryption Key in PCI Vault
One of the core features of PCI Vault is the ability to encrypt data before tokenization. This adds an extra layer of security: even if someone intercepted the data in transit, it would be encrypted and useless to them. PCI Vault typically requires creating an encryption key in their system:
- Create Key via API or Dashboard: PCI Vault likely has an endpoint like “Create Key” (sometimes called Generate Encryption Key). Using your API tool (could be done via a cURL command, or perhaps PCI Vault’s web dashboard), create a new key. For example, RapidDev’s guide suggests calling a “Create a Key” endpoint to set up an encryption key for your account. This key is used to encrypt the sensitive data you send for tokenization.
- Receive Key ID and Passphrase: When you create a key, the system will give you some identifiers. Often, it provides a Key ID (to reference that key in future calls) and possibly a passphrase or secret associated with the key. The passphrase might be auto-generated or something you set; it’s essentially like a password that can unlock the data that was encrypted with the key. Important: Safeguard this passphrase. You will need it whenever you want to decrypt (retrieve) data from a token. Store it securely (never in plaintext in your Bubble app). Bubble’s server-side actions or environment variables are a good place, or you might require an admin to input it when needed. Never expose the passphrase on the client side.
- Secure Storage of Key Info: Save the Key ID (and maybe an alias for it) in your Bubble app settings if needed. You might have multiple keys over time (some companies rotate keys regularly), but start with one. Ensure your Bubble workflows know which Key ID to use when making tokenization calls. The passphrase, if required each time, might need to be provided in the API call for decryption requests (we will address that in step 6). Keep that passphrase secret within the app’s backend.
By completing step 3, you now have the cryptographic tools in place: an encryption key managed by PCI Vault. This will be used to actually scramble the card data on its way to the vault, ensuring that only PCI Vault can decrypt it (with the passphrase’s help). It’s a critical security step that adds trustworthiness to the integration.
Step 4: Configure Bubble to Tokenize Data via PCI Vault API
This step is where the integration actually happens in Bubble. You’ll set up the API calls and workflows to send card data to PCI Vault and get back a token.
- Set Up API Call in Bubble’s API Connector: Open the API Connector plugin in Bubble. Under your “PCI Vault API” (created earlier), add a new call. Name it something like “Tokenize Credit Card”. This will correspond to PCI Vault’s endpoint for encrypting and tokenizing data. According to the RapidDev guide, there’s an “Encrypt and Tokenize Data” endpoint. The exact details will depend on PCI Vault’s API, but typically:
- It will be an HTTP POST request to a URL like https://api.pcivault.io/v1/tokenize (just an example).
- Headers might include your API key (Authorization: Bearer <your API key> or similar).
- The body will include the data you want to tokenize. For example:It might also accept multiple fields or a structured object if you want to tokenize more than just the number. Check the docs for required fields. Many APIs simply take a card number and maybe some description or context.
{
"keyId": "<Your Encryption Key ID>",
"data": "<The sensitive data (card number)>",
"additionalData": { "exp": "1225", "cvv": "123", ... } // If their API accepts extra fields
}
- Ensure the body is configured as JSON (if required) and that the API call is set to Action (not just Data) if you want to trigger it in a workflow (Action allows you to run on demand and wait for response).
- Initialize the Call (Optional): Bubble’s API connector often has a step to initialize calls with example values. You might need to input a dummy card number and your key to test the call. Use a test credit card number (like “4111111111111111” which is a common Visa test number) and see if PCI Vault returns a token in the response. The response might look like { "token": "abcdef123456...", "status": "success" } or something. Once it’s working, Bubble will let you pick the response fields.
- Design the Workflow: Now, go to your Bubble editor’s Workflow tab. For the event (e.g., “Save Card” button click), add an action: “Plugins → PCI Vault API - Tokenize Credit Card” (or whatever you named it). Map the fields:
- For card number, use the Input’s value (the user-entered number).
- Include the encryption Key ID, possibly as a parameter. If your API call definition has Key ID as a field, put the ID you got from step 3 (you might store it in a custom state or just text).
- Include any other required info (maybe card expiry date, etc., if needed by the vault).
- Store the Returned Token: After the API action, add another action in the workflow to “Create a thing” or “Make changes to thing” in your database. For example, you might create a new entry in a “PaymentMethod” data type, or update the current User with a field “saved_card_token”. Set that field to Result of Step X (Tokenize Credit Card) -> token (Bubble will allow you to select the returned token from the API call’s result, assuming you initialized it and have the field). Essentially, you’re now saving the token string in Bubble’s database. This token is safe to store because it’s just an identifier, not sensitive data.
- Do Not Store Raw Data: Double-check your workflow and database steps to ensure you are not accidentally storing the raw credit card number or other sensitive info in Bubble. You should only keep the token and perhaps non-sensitive info like last 4 digits or card type (if you choose to extract that for user convenience). For instance, some might store “**** **** **** 1111” as a display number and expiration month/year to show the user “Card ending in 1111, exp 12/25”. You can get those easily from the input or the tokenization response if it provides them.
- Success/Failure Handling: Add a way to handle if the API call fails. The API Connector will throw an error if something’s wrong (like invalid card or wrong key). You can use Bubble’s error handling (an event “When an unhandled error occurs” or the “Only when” on the next step to detect if token is empty). Show the user a friendly message, like “Please check the card details and try again” if something goes wrong. On success, you might show a popup “Your card has been saved securely!” to reassure them.
This is the most technical step, but take it slow and test each part. By the end of Step 4, your app can send a piece of sensitive data to PCI Vault and receive back a secure token, all within a few seconds during a workflow. Congratulations – the hardest part is done!
Step 5: Store and Use the Token in Your Bubble App
At this point, you’ve got a token representing the customer’s card stored in your Bubble database. Now you’ll want to use that token for actual operations like charging the card or retrieving card info when needed.
- Storing the Token (Recap): We did this in Step 4 by saving the token string in the database. Ensure that the token is associated with the right user or entity. For example, if you have a User data type and each user can have a saved card, maybe you added a field User.card_token. Or you created a separate CreditCard thing with fields like token, last4, brand and a link to the User. However you did it, the token is now available for later workflows.
- Using the Token for Payments: The token itself can’t charge a card – it’s not a payment method by itself, but you can use it with payment processors. How?
- Some payment gateways allow you to supply an external token along with a secure method to get the actual card data. For instance, you might call PCI Vault to retrieve the card data and then pass it to Stripe via a server-side call. But a more secure approach: PCI Vault can often send the card data directly to a payment processor for you. Check if PCI Vault integrates with common processors or if you can retrieve data server-side.
- Alternatively, you might use the token to charge through PCI Vault’s own API if they offer a charging mechanism. However, since PCI Vault is mainly storage, you probably will do:
Ask PCI Vault for the card details when you need to charge.
Use a payment API to actually run the charge.
- A practical method: have a Cloudflare Worker, AWS Lambda, or Bubble’s Server Side Plugin that can take a token, call PCI Vault (with key and passphrase) to get card number, then call Stripe’s charge API. This keeps the heavy lifting off the user’s device.
- Displaying Card Info (if needed): Maybe you want to show the user something like “Card on file: **** **** **** 1111 exp 12/25”. You likely already stored the last 4 and exp date at tokenization time. If not, you can retrieve the full card info via PCI Vault’s decrypt endpoint (more on that in Step 6) and then just use it to display partial info. Always avoid showing full card numbers or CVV in the UI, even to admins, unless absolutely necessary – and even then, think twice. The standard practice is to mask all but the last 4 digits of the card.
- Multiple Payment Methods: If your app allows users to save multiple cards, you can repeat the tokenization process for each new card and store multiple tokens. Just design your database to handle a list of tokens or multiple card entries per user.
In essence, after step 5, your Bubble application is now successfully using tokens as a stand-in for sensitive data. You’ve achieved the primary goal: the app does not store or process actual credit card numbers – it only stores tokens and uses them for any future operations. This dramatically limits what an attacker could get from your app and firmly puts you on the right side of PCI guidelines. Next, we’ll cover how to get back the original data from PCI Vault if and when you need it, securely.
Step 6: Retrieve Tokenized Data Securely when Needed
Tokenization wouldn’t be very useful if you could never get the original data back. Sometimes you need the actual card info – for instance, to send it to a payment processor that isn’t directly integrated with PCI Vault, or to display certain info to a user. Step 6 is about retrieving (decrypting) the data from a token securely.
- Decrypt API Call: PCI Vault should provide an endpoint like “Decrypt Token” or “Retrieve Data”. Set up another API call in the Bubble API Connector, maybe call it “Retrieve Card Data”. This will be a POST or GET request to something like https://api.pcivault.io/v1/decrypt with necessary parameters:
- Token: The token string that you saved (e.g., “tok_123abc...”).
- Key ID: To let the system know which encryption key was used.
- Passphrase: This is the critical part – you will likely need to provide the passphrase associated with your encryption key as part of the request (perhaps in headers or body). This passphrase proves you’re authorized to decrypt. Make sure you handle this carefully: do it in a server-side context. If you invoke this API call from Bubble’s client-side (browser) it could expose the passphrase. Ideally, run the decryption via a backend workflow (Bubble’s Scheduled API Workflow or a server plugin) so that the passphrase stays on the server side.
- Workflow for Retrieval: If you have a use case like charging a card:
- You might initiate a backend workflow that takes a user’s token, uses the Retrieve Card Data API call (including the passphrase stored in a secure setting), gets the card number (and perhaps exp and other details) in the response.
- Immediately use those details with your payment processor’s API to perform the charge.
- Importantly, do not store the card details in Bubble. You should use them on the fly and discard. For example, if using Stripe’s API via Bubble’s connector, you could plug in the card number, exp, CVV from the PCI Vault response directly into the Stripe “Charge” call, without saving them to the database.
- Once done, you can forget those details. The token remains for future use.
- Protecting the Passphrase: Since the decryption passphrase is effectively the keys to the kingdom (it unlocks the sensitive data), restrict who/what can trigger the decryption. Only certain backend workflows or admin functions should do it. Implement checks: e.g., only allow a decryption if the current user is an admin or if it’s part of a server event that you initiated for payment.
- One-Time Access Option: Some tokenization services (perhaps PCI Vault) support one-time retrieval links. For instance, instead of returning the raw data to you, they might offer to send it directly to a third-party endpoint you configure (like sending to Stripe or a webhook). This is advanced but it’s the most secure option: your app never sees the data even during retrieval – it goes from vault to the destination. Explore if PCI Vault offers such a feature (it might be indicated by that diagram reference where a URL and secret are shared). If so, you can use that for truly minimizing data exposure.
By executing step 6, your app can fetch and use the actual card information when needed, but under tightly controlled conditions. Most of the time, you won’t need to decrypt – tokenization covers recurring billing scenarios by storing token only, etc. But it’s good to have this capability configured. Now, the integration cycle is basically complete: you can tokenize and detokenize as needed. The final step is ensuring everything remains solid and addressing ongoing security.
Step 7: Test and Apply Security Best Practices
With the integration implemented, it’s crucial to test it thoroughly and bolster it with best practices:
- End-to-End Testing: Use test card numbers to run through the entire flow in a development version of your Bubble app. Enter a card, tokenize it, attempt a dummy charge or data retrieval. Verify in the Bubble database that only tokens (and non-sensitive info) are saved – no actual card numbers or CVVs anywhere. Check your Bubble Logs (you can see logs in Bubble editor) to ensure card numbers aren’t accidentally logged. For instance, if you printed something or an error occurred, make sure sensitive data didn’t slip into logs. If they did, adjust your workflows to avoid that.
- Error Handling: Intentionally try some error scenarios. What if the user enters an invalid card number? Does the PCI Vault API return an error message? Make sure your Bubble workflow captures that (the API connector might return an error). You can use the “An element has an error” or similar events to catch it. Provide user feedback like “Invalid card number, please try again.” Similarly, what happens if the PCI Vault service is unreachable (network issue) – your app should handle it gracefully, perhaps by showing a general error like “Unable to save card at this time. Please check your connection and try again.”
- Role-Based Access Control (RBAC): Implement Bubble privacy roles or checks in workflows so that only authorized users can trigger certain actions. For example, if you have an admin page that can view full card info (hopefully not needed, but suppose), ensure only admin roles can access that page and run that decryption workflow. In general, normal users should never directly trigger a raw decrypt except maybe indirectly when making a payment, and even then the info should go straight to the payment processor.
- Audit Logging: It’s a good idea to log whenever a tokenization or decryption happens (without logging the sensitive data itself). For example, each time you call the tokenization API, you could log an event “Tokenized card for user X at time Y”. Each time you decrypt, log “Decrypted token for user X to charge payment at time Z”. These logs can just be entries in a simple “SecurityLog” data type or even sent off to an external logging service. In case of any issues, these logs help trace who accessed what and when – a key for both security and compliance audits.
- Secure Key Management: Over time, consider rotating your encryption key. PCI Vault might allow you to create a new key, and re-tokenize existing data with the new key. This is an advanced step usually, but security best practices suggest not using the same encryption keys indefinitely. Maybe once a year or if you suspect a key was compromised, you’d rotate. Keep track of which token was made with which Key ID if you ever do multiple.
- Rate Limiting & Performance: Be aware of any rate limits PCI Vault’s API might have. If your app suddenly grows and you’re tokenizing a lot or decrypting frequently, ensure you handle if the API says “too many requests”. Maybe space out calls or contact PCI Vault for higher capacity. Typically, these services are built to scale, but just be mindful.
- User Experience: On the UX side, emphasize to users that their data is secure. You don’t want to scare them, but a small note like “Your payment info is securely stored and encrypted off-site” can reassure them and set expectations. If there’s a slight delay when saving a card due to the API call, use a loading spinner or message like “Securing your card details…”.
By following step 7, you’re ensuring that not only does your integration work, but it’s robust against real-world conditions and aligns with security best practices. Regular audits and reviews of your workflows can keep it that way.
Phew, that was a lot of ground covered! At this stage, you have a fully functional integration of PCI Vault within your Bubble.io application. Next, let’s address some common questions that might arise regarding this setup.
Frequently Asked Questions (FAQs)
Before we wrap up, let’s tackle some FAQs that Bubble developers and business owners often have about PCI compliance and using PCI Vault. These address practical concerns and edge cases you might be curious about:
Q1: Can I use PCI Vault with any Bubble.io plan, or do I need a special enterprise plan for added security?
A: You can use PCI Vault with any standard Bubble plan because the integration works through API calls which are available even on the free/hobby plan. However, if you’re handling a lot of volume or want to run workflows on the backend (like scheduled API workflows for charging cards), a higher-tier Bubble plan that supports backend workflows would be beneficial. The security provided by PCI Vault doesn’t depend on Bubble’s plan – it’s external. That said, higher Bubble plans may offer better performance or features (like increased capacity, logs, etc.) that can indirectly help your app scale securely.
Q2: Does integrating PCI Vault make my Bubble app “fully” PCI DSS compliant?
A: It significantly reduces your compliance obligations, but it doesn’t 100% absolve you of all responsibility. Here’s why: PCI Vault will cover the storage and handling of card data, meaning your Bubble app is mostly out-of-scope. Many PCI controls (requirements) won’t apply to you, and you’ll likely just do a simpler Self-Assessment Questionnaire (like SAQ A or SAQ A-EP, depending on implementation) rather than a full audit. The WordPress PCI Vault plugin description notes that using it “allows you to securely capture and tokenize credit card data without being PCI DSS compliant” – to interpret, it means you don’t need your own environment certified. However, you should still ensure basic security in your app (SSL enabled, no storing of sensitive info, good access control) because if you screw up something outside of PCI Vault (like accidentally emailing tokens or leaving APIs open), that could cause issues. Always consult with a compliance expert if you’re unsure, but in general, using PCI Vault should satisfy the card issuers and banks as long as you’re not storing cardholder data in Bubble.
Q3: Are there alternatives to PCI Vault that work with Bubble.io?
A: Yes, PCI Vault is one solution, but not the only fish in the sea. Other services like Basis Theory and Very Good Security (VGS) offer data vault and proxy solutions, and they can be integrated via API in a similar fashion. Some developers also choose to use Stripe or Braintree purely as a vault (store card details with them and get a token for later charges, without immediately charging the card). Stripe, for example, lets you collect a card and get a “PaymentMethod ID” or “Setup Intent” that you can use later. The key difference is that those are tied to using Stripe’s payment processing. PCI Vault and similar vault services are neutral – you can use the tokens anywhere. Strac is another mentionable service; it even has a Bubble plugin for storing PII/PHI data (not sure if it’s focused on payments, but it shows the trend in secure storage solutions). The best choice depends on your budget, technical comfort, and specific needs. PCI Vault is great if you want a turnkey PCI compliance fix. Others might offer more customization or handle different data types. It’s worth researching a bit, but rest assured, Bubble can work with any of these via API.
Q4: How is using PCI Vault different from just using a payment processor like Stripe or PayPal for compliance?
A: With Stripe/PayPal, typically you would use their checkout forms or libraries (Stripe Elements, etc.), which means the card data goes directly to them. That indeed keeps you out of PCI scope as well. The difference is control and flexibility. If you use Stripe’s solution:
- You might be locked into Stripe for processing; the token you get is a Stripe token that can only be used with Stripe’s API. If you ever want to use a different processor or move the data, you can’t easily – you’d have to ask users to re-enter cards or go through a secure transfer process.
- Payment processors usually handle the whole transaction, not just store cards. PCI Vault is storage-only (tokenization), which can be used in conjunction with any transaction service. It’s ideal if, say, you want to store cards and later charge them via a bank’s ACH system, or have multiple payment providers.
- Also, PCI Vault might allow storing other sensitive data (like personal info, etc. depending on the service capabilities) so it can centralize security for more than just payments.
In summary, using Stripe is perfectly fine for many cases (and if it suits you, it’s often simpler if all you need is charging cards with Stripe). But if you require neutrality or have a complex flow (like storing first, charging later, possibly splitting payments, etc.), a vault gives you that freedom.
Q5: Will using PCI Vault slow down my app or introduce a lag for users?
A: The process of tokenization is very fast – typically just a fraction of a second to get a token back. The overall perceived speed depends on internet latency and the efficiency of PCI Vault’s API. In most cases, users won’t notice any significant delay. For instance, when they hit “Save Card”, it might take maybe 1 second to get a confirmation instead of, say, 0.2 seconds if it was purely local. That trade-off is minor given the security gained. To ensure smooth UX:
- Use loading indicators (like a spinner or “Please wait…” message) while the API call is happening, so the user knows something is processing.
- Test the calls: PCI Vault’s infrastructure should be robust (some advertise very high transaction per second rates – e.g., 10,000+ card encryptions per second according to their site blurb). So performance is likely a non-issue unless the user’s connection is slow.
- If you do a decrypt call during a checkout, that’s another quick round trip. Perhaps half a second to fetch data then process payment – still pretty quick.
In summary, any slight latency introduced by calling out to PCI Vault is usually negligible. It’s a small price for the confidence that you’re not exposing sensitive info. Most users won’t notice anything unusual at all, especially if you design the UI to be responsive during the process.
Q6: What happens if PCI Vault’s service has an outage or goes down?
A: It’s wise to consider contingency plans. If PCI Vault were to experience downtime (hopefully rare, especially if they have a good uptime record), what’s your app’s behavior?
- During Tokenization: If a user tries to save a card and PCI Vault is unreachable, you should catch that error. You might show a message like “We’re unable to save your card at the moment due to a server issue. Please try again shortly.” You might log the error and certainly not proceed to mark a card as saved when it isn’t.
- During Charge/Decryption: If you cannot retrieve the card data to process a payment, you should similarly handle that gracefully: perhaps queue the transaction to retry a few minutes later (inform the user “Processing delay, we will complete your transaction momentarily”) or ask for an alternate payment method if it’s urgent.
- Redundancy: If your business is mission-critical on this, you might even consider having a backup vault service. That’s complex and usually unnecessary, but conceivably one could integrate two providers and failover if one fails. This is probably overkill for most.
- Remember that even big providers can have hiccups, but they are incentivized to minimize them. Check PCI Vault’s SLA (Service Level Agreement) if any, to understand their uptime guarantees.
In practice, it might be enough to have a policy: if an outage occurs, pause new card captures and resume when fixed. The likelihood is low, but planning for it shows good forethought.
Those are some of the common questions, but you might have more specific ones depending on your use case. The Bubble community forums or PCI Vault’s support channels are great places to seek further clarification. Now, let’s wrap things up.
Conclusion
Achieving PCI compliance might sound like climbing Mount Everest, especially for indie developers or small startups on a platform like Bubble.io. But as we’ve explored, PCI compliance can be made simple with the right approach – specifically, by integrating PCI Vault into your Bubble app. This marriage of a no-code platform with a security-focused service gives you the best of both worlds: you retain Bubble’s famous ease-of-use and speed of development, while PCI Vault takes care of the heavy-duty security and compliance requirements behind the scenes.
By following the 7 steps outlined in this guide, you’ve effectively implemented a robust shield around your customers’ credit card data. Let’s appreciate what that means: your Bubble application never stores or directly processes raw card numbers – those are safely locked away in PCI Vault’s secure servers. If a malicious actor breaches your app’s database, all they’d find are useless tokens. The risk of catastrophic data breaches plummets, and with it, the nightmare scenarios of huge fines or lost customer trust fade away. You’ve turned a daunting compliance challenge into a manageable workflow in your app.
Moreover, going through this process likely made you and your team more security-conscious overall. You’ve implemented best practices like access controls and auditing, which will serve you well beyond just payment data. You can confidently tell your users that their sensitive information is handled with care — not only meeting industry standards but exceeding them by using state-of-the-art tokenization. This kind of transparency and commitment can be a selling point, setting you apart in a world where data privacy is on everyone’s mind.
In an optimistic outlook, embracing tools like PCI Vault doesn’t just solve a problem, it opens doors. Now you can focus on growing your business, adding features, and improving user experience, rather than worrying about security gaps. Need to add support for a new payment processor? No problem – you have a vault of tokens you can use anywhere. Expanding globally? You’re already in good shape to handle international data protection expectations because the fundamentals are strong.
To put it simply, you’ve simplified compliance without sacrificing innovation. That’s a big win. As you move forward, continue to keep an eye on security trends, maintain your integration (updating API keys or endpoints if needed, rotating keys occasionally), and stay prepared for new compliance developments. The landscape of fintech and data security keeps evolving, but you now have a solid foundation to adapt from.
We hope this comprehensive guide has truly made PCI compliance feel simple for you. With Bubble.io and PCI Vault working hand in hand, you can stride into the future of your app with confidence and focus on what you do best – building a great product – while the experts handle the vault of secrets.
Happy building, and stay secure!
Translate this article – Need this guide in another language for your team or audience? We can help translate it while preserving all the crucial details.
Generate blog-ready images – Enhance this article with custom visuals or diagrams (e.g. a tokenization flowchart, or an infographic of the 7 steps) to make the concepts even clearer.
Start a new article – Have another topic in mind (perhaps “Advanced Bubble Security Practices” or “Integrating Bubble with other compliance services”)? Let’s dive into a new deep research task!
